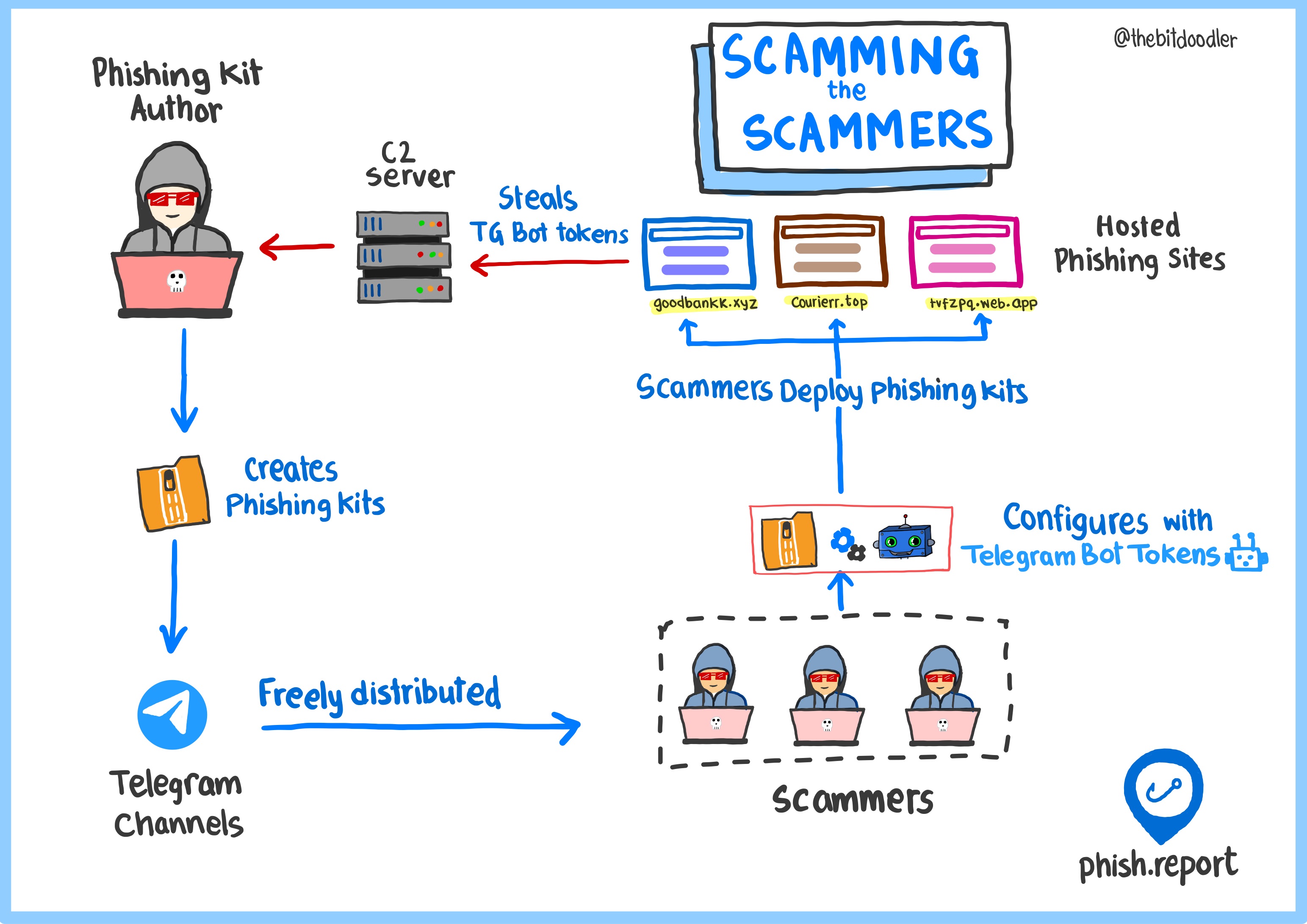
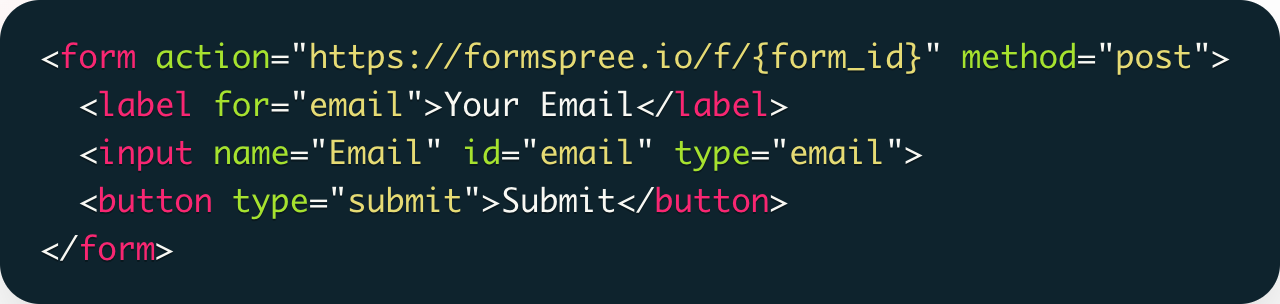
Deploying a phishing website is rarely a highly technical task. For most brands, a phishing kit au...
Blogposts and resources from the Phish Report team
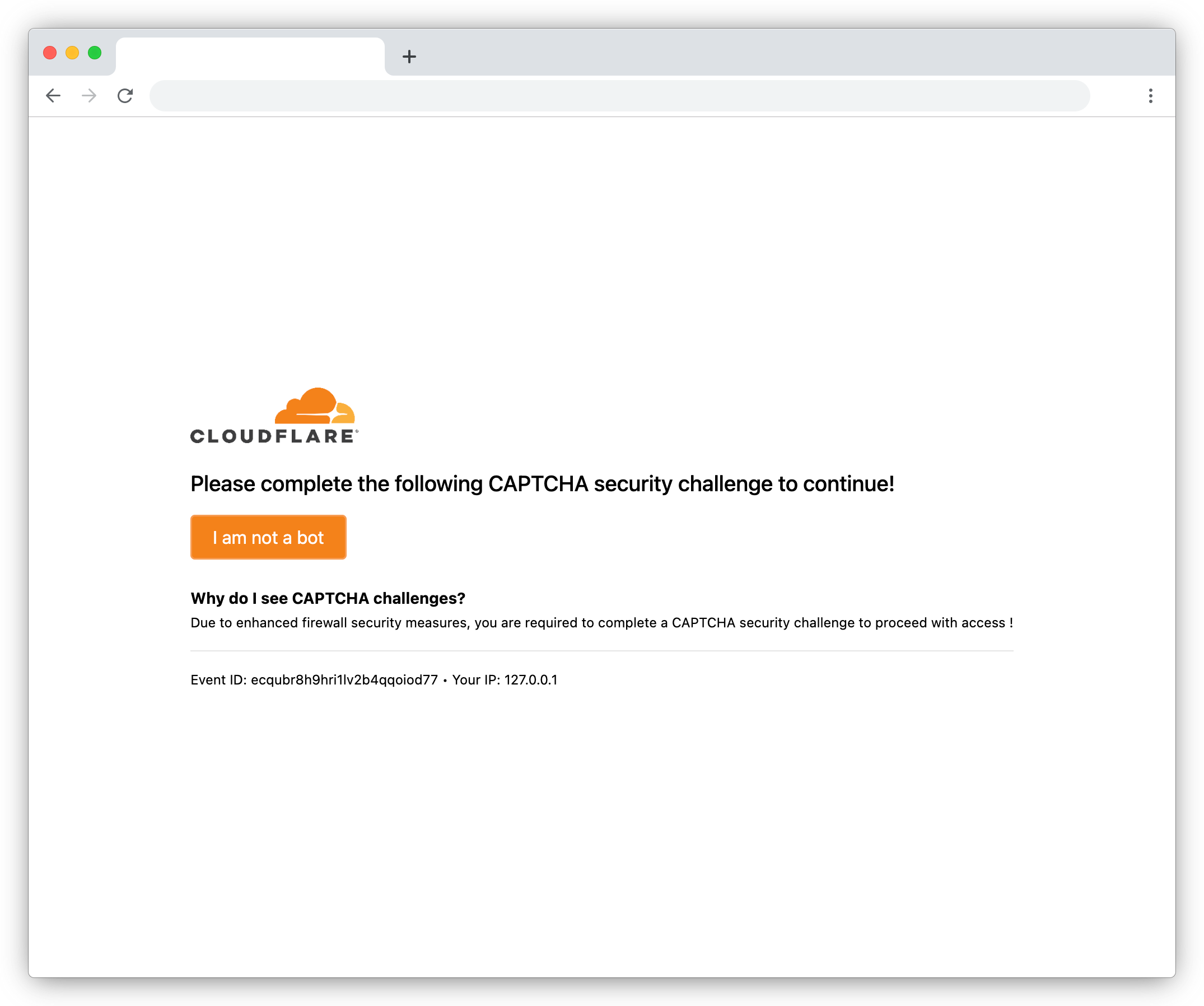
Evading security scanners with fake Cloudflare interstitials
For years phishing sites have been using services like Cloudflare to hide from security scanners, ...
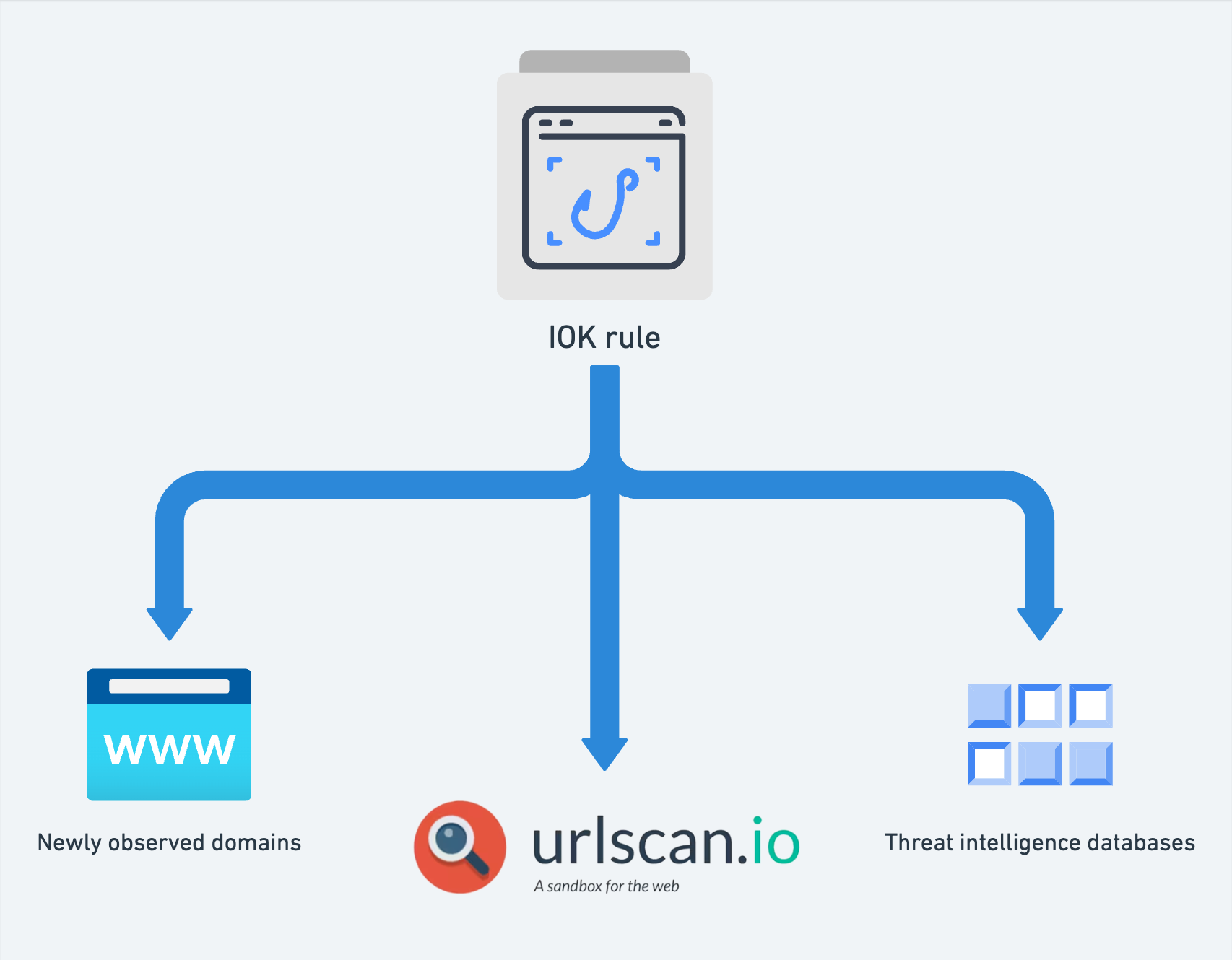
Using IOK rules to hunt for phishing sites across multiple threat intelligence sources
IOK ("Indicator of Kit") is a small, open source language d...
Phishing anti-analysis checks and how to bypass them
Anti-analysis checks are used by phishing sites to detect when they're being accessed by security ...
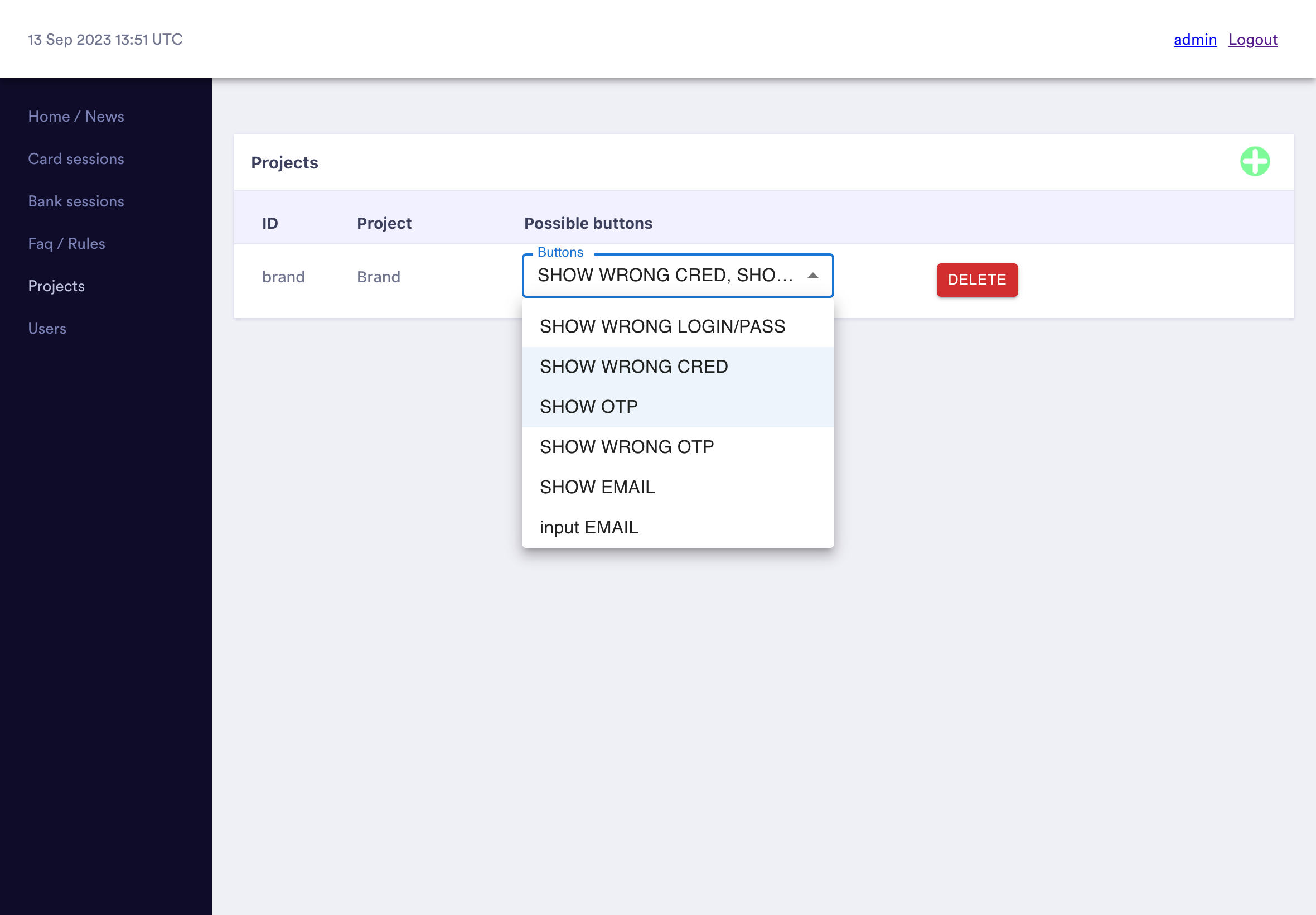
RedLungfish: an organised phishing group targeting fintech customers
The Phish Report threats team have identified an organised threat actor (codenamed RedLungfish) wh...
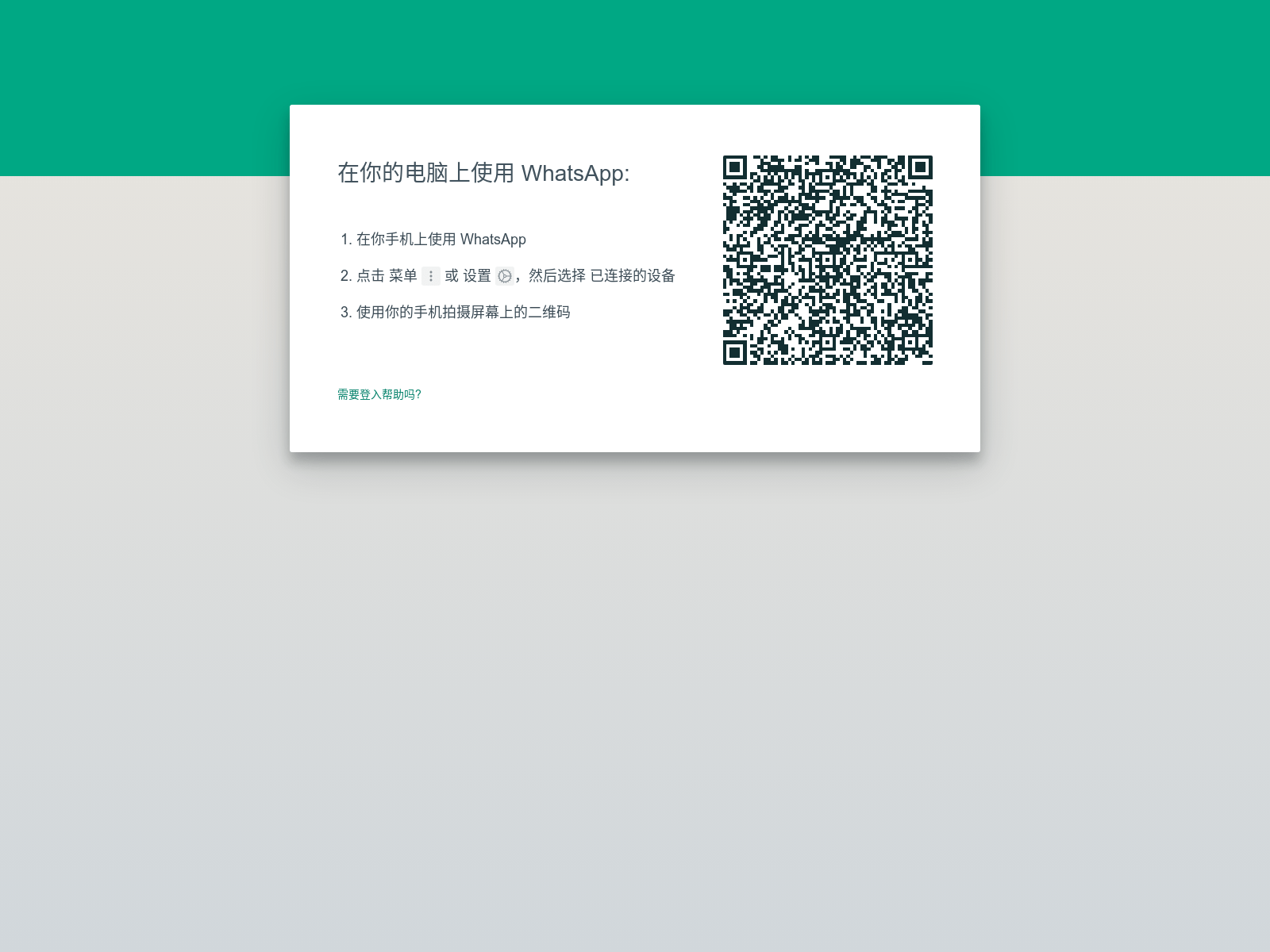
Writing an IOK rule for a WhatsApp phishing kit
Let's write an IOK signature for a WhatsApp phishing kit which targeted Chinese-speaking users for...

How to harden your login page against cloning
Cloning a login page in order to make phishing sites takes only a few seconds. There's a good chan...
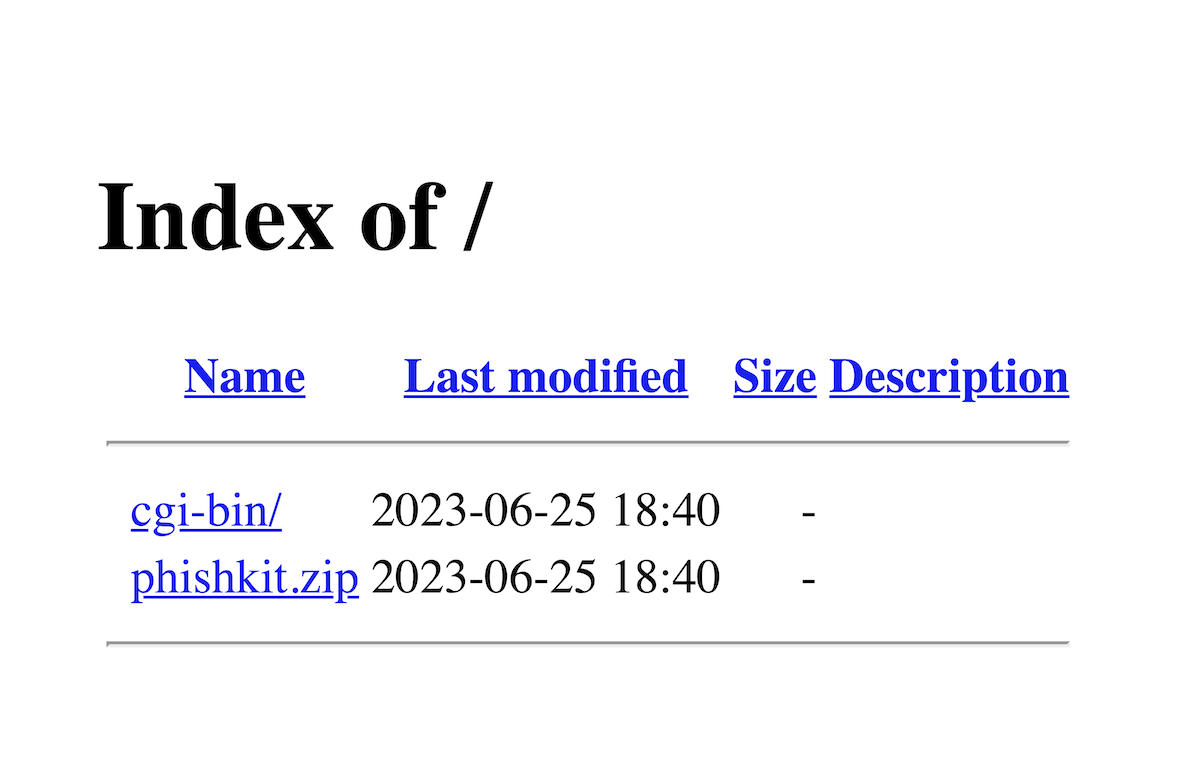
How to find and download phishing kits
Phishing kits are generally sold on underground forums and can be tricky (at least ethically!) for...

Why it's hard to identify who hosts a website
Who hosts that website? Seems a simple question, but it's very hard to consistently get the right ...

Threat hunting for phishing sites with urlscan.io
urlscan.io is an incredible tool for taking a snapshot of a phishing website...
How the static site trend has affected phishing
The trend towards statically generated websites hasn't been limited to legitimate websites. Increa...

A startup's guide to phishing and brand protection
As a startup, building and protecting your brand is essential to success. Unfortunately, cybercrim...

Top 5 phishing detection APIs you can start using today
There's too many suspicious URLs going round to manually check every one to see if it's malicious....
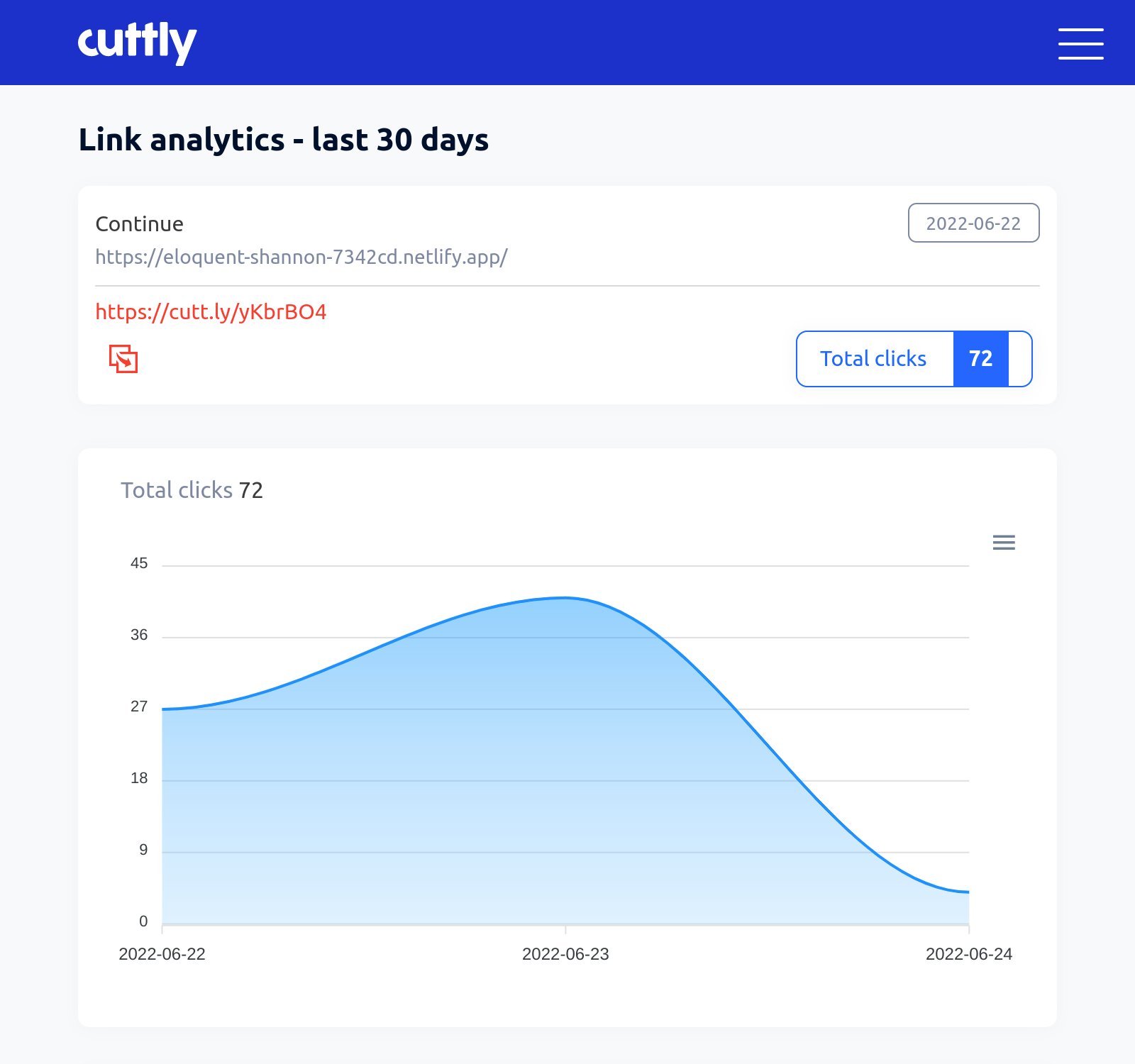
Open Source Intelligence (OSINT) from common link shorteners
Phishers love to use URL shorteners, but this can actually be a benefit for defenders too. Wouldn'...
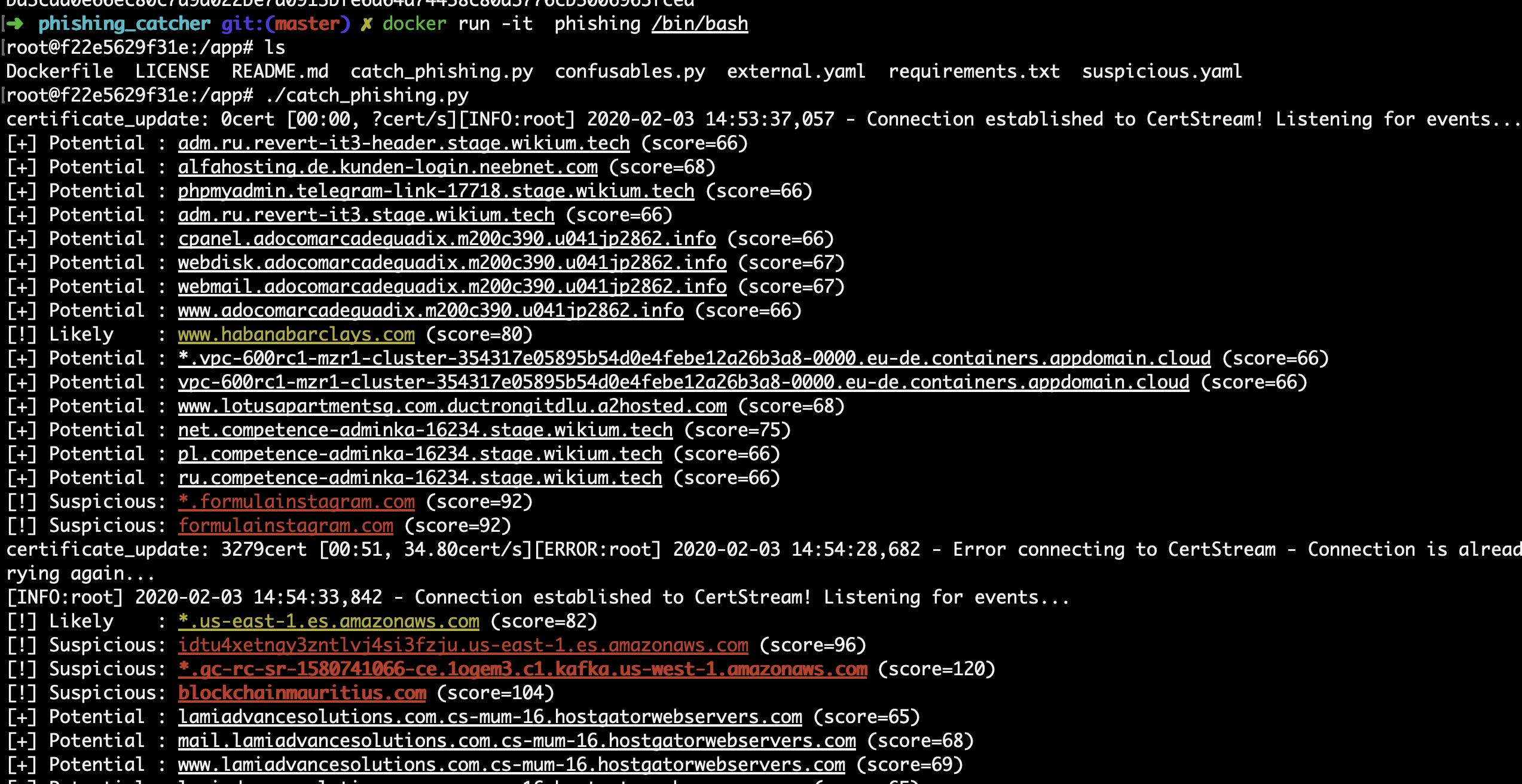
How to detect phishing websites in real-time using open source
The key to successfully combating phishing is detecting it early: the sooner you can report a phis...
Detecting phishing sites with high-entropy strings
You'd expect phishing sites to be hard to detect and track, but actually, many of them contain HTM...

Top 4 security vulnerabilities we see in phishing kits
Just like any other website, phishing sites can have security vulnerabilities. But, for once, thes...

Flake IDs and insensitive ticketing systems
This week the IDs we use for identifying Phish Report cases got 20% longer, but twice as reliable....