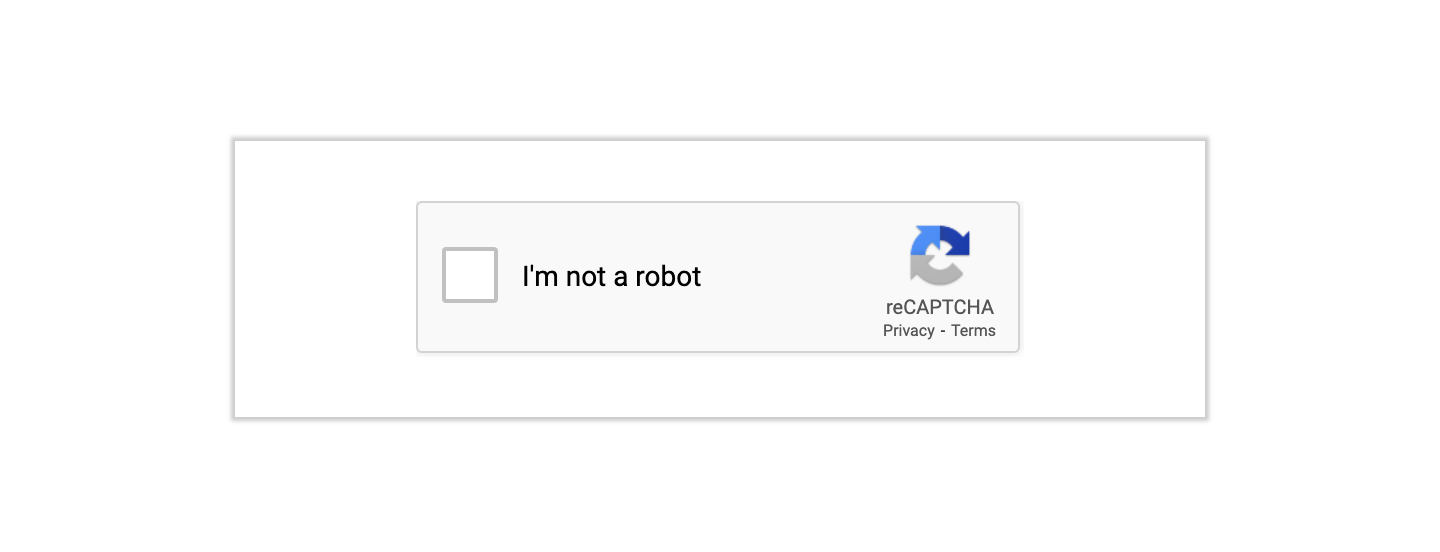
Phishing anti-analysis checks and how to bypass them

Anti-analysis checks are used by phishing sites to detect when they're being accessed by security teams and display benign content rather than the real phishing site.
Why do phishers use anti-analysis checks?
Phishers are in a constant race with security teams: how many victims can they compromise before their site is shut down.
By adding an "antibot" script to their phishing kit, phishers can increase the time it takes for security teams to identify and report the site:
- Automated systems may not be able to detect the site (instead requiring manual investigation)
- Hosting provider abuse teams may be unable to see the malicious content and will need additional evidence before removing it
The most common anti-analysis checks
User-Agent restrictions
When a phisher sends out their phishing site via SMS messages, they only expect the site to be viewed by mobile browsers. But, security teams generally aren't using mobiles so this makes for a great opportunity for the phisher to filter by the browser user agent.
Luckily, all major browsers let you spoof your user agent using their developer tools:
Geo IP restrictions
Many phishing sites impersonate companies who only have customers in one or a small number of countries. In these cases, phishers can restrict access to the phishing site to just those targeted countries.
Although this usually doesn't stop security teams discovering the site (as they're likely in the same country as their customers), but it does impact abuse teams at hosting providers. The phisher can easily choose a hosting provider outside their target country and so when their abuse team reviews a report they may be unable to see any malicious content.
To bypass geo IP restrictions, ensure you're using a VPN whose traffic exits in the targeted country.
Residential IP restrictions
Phishers want their sites to avoid detection for as long as possible which means avoiding automated security scanners. As these scanners are running on servers hosted in datacenters, phishers can reject requests from IPs known to belong to datacenters.
To bypass residential IP restrictions, use a VPN or proxy solution which routes through residential IPs.
Headless browser detection
With some anti-analysis checks implemented in JavaScript, security scanners can't just fetch HTML content, they need to actually load the website in a browser.
The most common way to do this is using something like Headless Chrome, but by default this is very obvious to phishers.
A phishing site can simply look for the navigator.webdriver property and then not display any phishing content:
The navigator.webdriver property is true when in:
Chrome: The --enable-automation or the --headless flag or the --remote-debugging-port is used.
Firefox: The marionette.enabled preference or --marionette flag is passed.
How are anti-analysis checks implemented?
Like any other website, there's two places phishers can add anti-analysis checks:
- In their server-side code (usually PHP)
- In JavaScript which runs client-side in the browser
Server-side
Server-side anti-analysis checks are the hardest to reverse engineer because the code isn't available to analyse.
But, these checks are limited to the data sent in the HTTP request to the server:
- The requested URL
- The IP address of the client
- The HTTP headers (including the User Agent)
In particular, this means they can't do anything to check whether a headless browser is being used.
Client-side
In contrast, client-side anti-analysis checks are significantly easier to reverse engineer and bypass. Either:
- The phishing site is loaded and then if the anti-analysis check fails, the browser is redirected to some benign content
- The anti-analysis check runs and if it passes, the browser is redirected to the phishing content
In both cases, reading through the site JavaScript will reveal where to find the phishing content. Obfuscation can slow this process, but not by much.
Want more insight into phishing kits?
Start a trial today.
More posts from the Phish Report team
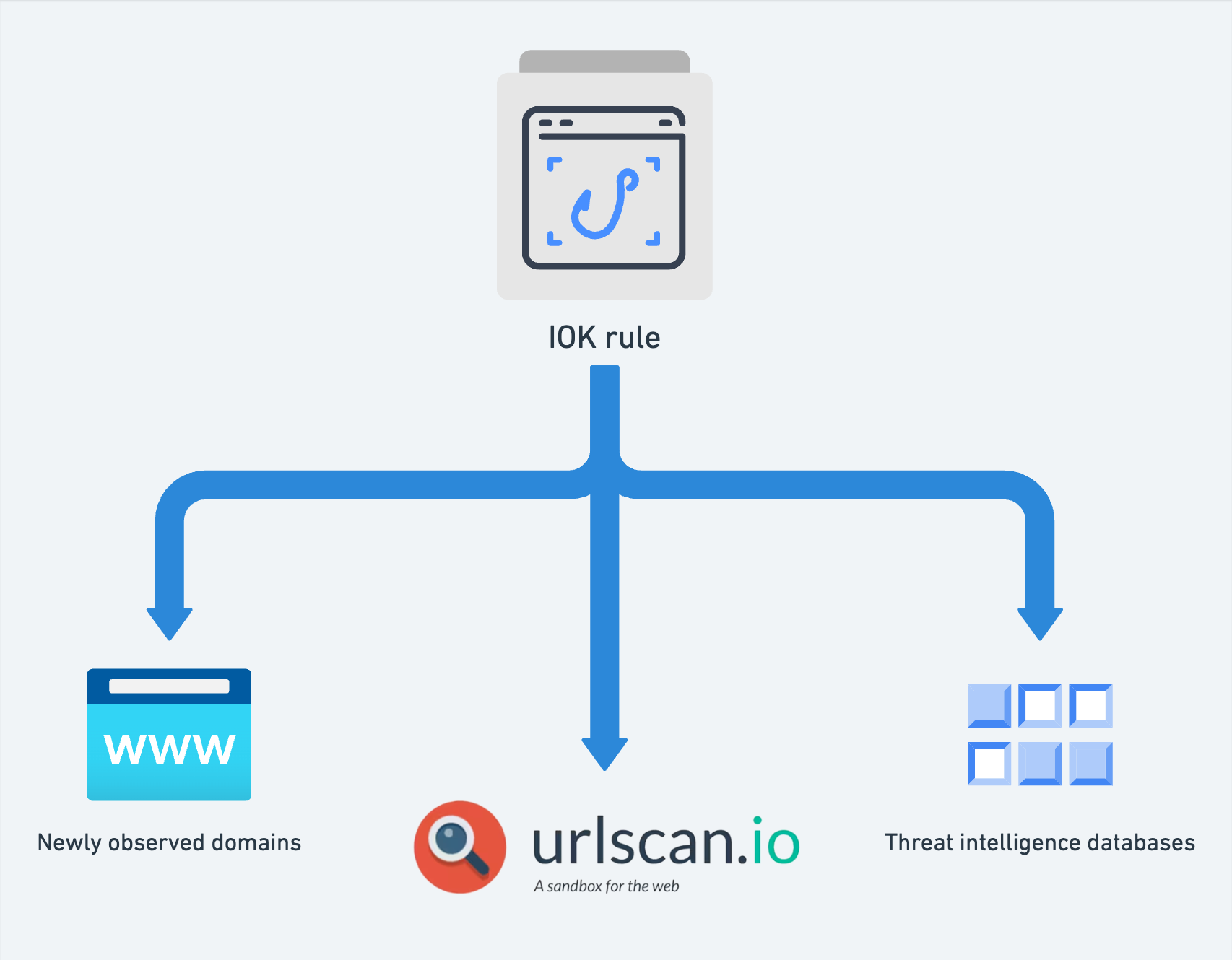
Using IOK rules to hunt for phishing sites across multiple threat intelligence sources
How to detect phishing websites in real-time using open source
