
Top 5 phishing detection APIs you can start using today

There's too many suspicious URLs going round to manually check every one to see if it's malicious. Automating the process using a phishing detection API is vital.
There's many free and paid options available but here's our roundup of the top phishing detection APIs you can start using today.
Google Safe Browsing
Google Safe Browsing is probably the first phishing detection API you should integrate with.
Safe Browsing is a Google service that lets client applications check URLs against Google's constantly updated lists of unsafe web resources. Examples of unsafe web resources are social engineering sites (phishing and deceptive sites) and sites that host malware or unwanted software. Come see what's possible.
With Safe Browsing you can:
- Check pages against our Safe Browsing lists based on platform and threat types.
- Warn users before they click links in your site that may lead to infected pages.
- Prevent users from posting links to known infected pages from your site.
Pros/cons
- Suitable for high volume checking (especially when using the Update API) 👍
- Extremely low false positive rate 👍
- Blocklist-based so gives poor results for brand-new phishing sites 👎
How to use the Safe Browsing API
To use the Safe Browsing API you first need to create a free API key following the instructions in the getting started guide. Unfortunately integrating with the Safe Browsing API is slightly cumbersome to do yourself so, once you have an API key, you'll need to find a library for your language of choice:
- Python: pysafebrowsing
from pysafebrowsing import SafeBrowsing s = SafeBrowsing(KEY) r = s.lookup_urls(['http://malware.testing.google.test/testing/malware/']) print(r) > {'http://malware.testing.google.test/testing/malware/': {'platforms': ['ANY_PLATFORM'], 'threats': ['MALWARE', 'SOCIAL_ENGINEERING'], 'malicious': True, 'cache': '300s'}} - Go: google/safebrowsing
sb, _ := safebrowsing.NewSafeBrowser(safebrowsing.Config{ APIKey: "your-api-key", }) verdict, _ := sb.LookupURLs([]string{"phishy.xyz"})) fmt.Println(verdict) - JavaScript: google-safe-browsing
const { GoogleSafeBrowsingClient } = require("google-safe-browsing"); const client = new GoogleSafeBrowsingClient("YOUR-API-KEY"); await client.isUrlSafe("example.com"); // => true
urlscan.io
urlscan.io is primarily a sandbox for getting a snapshot of a website and the resources it loads, but it also detects phishing sites for a wide range of brands.
urlscan.io is a free service to scan and analyse websites. When a URL is submitted to urlscan.io, an automated process will browse to the URL like a regular user and record the activity that this page navigation creates This includes the domains and IPs contacted, the resources (JavaScript, CSS, etc) requested from those domains, as well as additional information about the page itself urlscan.io will take a screenshot of the page, record the DOM content, JavaScript global variables, cookies created by the page, and a myriad of other observations If the site is targeting the users one of the more than 900 brands tracked by urlscan.io, it will be highlighted as potentially malicious in the scan results.
Pros/cons
- Suitable for fairly high volume checking (5000 scans per day on the free tier) 👍
- Gathers lots of additional context including a screenshot to speed up human verification 👍
- Detection rates only good if your brand is tracked, otherwise you'll get no detections 👎 (but, it's possible to add your own detections using a tool like IOK)
VirusTotal
While more commonly known for scanning files, VirusTotal can also be used to scan URLs and get back the verdict from dozens of other security tools in one go.
VirusTotal inspects items with over 70 antivirus scanners and URL/domain blocklisting services, in addition to a myriad of tools to extract signals from the studied content. Any user can select a file from their computer using their browser and send it to VirusTotal. VirusTotal offers a number of file submission methods, including the primary public web interface, desktop uploaders, browser extensions and a programmatic API. The web interface has the highest scanning priority among the publicly available submission methods. Submissions may be scripted in any programming language using the HTTP-based public API.
As with files, URLs can be submitted via several different means including the VirusTotal webpage, browser extensions and the API.
Upon submitting a file or URL basic results are shared with the submitter, and also between the examining partners, who use results to improve their own systems. As a result, by submitting files, URLs, domains, etc. to VirusTotal you are contributing to raise the global IT security level.
This core analysis is also the basis for several other features, including the VirusTotal Community: a network that allows users to comment on files and URLs and share notes with each other. VirusTotal can be useful in detecting malicious content and also in identifying false positives -- normal and harmless items detected as malicious by one or more scanners.
You can find their API documentation here: https://developers.virustotal.com/reference/scan-url
Pros/cons
- Returns the verdict from many security tools in one response 👍
- Not suitable for high volume checking 👎 (across the entire API you're limited to 500 requests per day and 4 per minute)
How to scan a URL with the VirusTotal API
Scanning a potential phishing URL with VirusTotal can be done simply by sending a POST request to the /api/v3/urls endpoint:
curl --request POST \
--url https://www.virustotal.com/api/v3/urls \
--form url=<Your URL here>
--header 'x-apikey: <your API key>'
In response, you'll get an ID that you can use to retrieve the results of the scan (once it has completed)
curl --request GET \
--url https://www.virustotal.com/api/v3/urls/{id} \
--header 'x-apikey: <your API key>'
Alternatively, there are two official client libraries you can use to make the integration easier:
CheckPhish
CheckPhish is a free phishing detection service offered by Bolster.
CheckPhish uses deep learning, computer vision and NLP to mimic how a person would look at, understand, and draw a verdict on a suspicious website. Our engine learns from high quality, proprietary datasets containing millions of image and text samples for high accuracy detection.
Pros/cons
- Uses machine learning so can be more effective in identifying novel phishing campaigns 👍
- Not suitable for high volume checking 👎 (only get 250 scans per month on the free tier)
How to scan a URL with the CheckPhish API
The CheckPhish API works similarly to other APIs requiring an initial scan request returning a job ID and a subsequent request to retrieve the results.
curl -X POST \
--header 'Content-Type: application/json' \
-d '{ "apiKey": "<your-api-key>", "urlInfo": { "url": "<potential-phishing-url>" } }' \
https://developers.checkphish.ai/api/neo/scan
Results can then be retrieved like so:
curl -X POST \
--header 'Content-Type: application/json' \
-d '{"apiKey": "<your-api-key>", "jobID": "<your-job-id>", "insights": true}' \
https://developers.checkphish.ai/api/neo/scan/status
There are no API client libraries provided for CheckPhish, so you'll need to implement your own.
Phishing Initiative
Phishing Initiative is a crowdsourced project by CERT Orange Cyberdefense.
Phishing Initiative ables any Internet user to help fight against phishing attacks.
When reporting us the address of a suspected phishing website, we’ll analyze it and have it blocked in the participating Web browsers.
By contributing to this project you decrease the impact of cybercrime and prevent others from becoming victims of online fraud.
Pros/cons
- By default, your API key can only query the current list, not submit new URLs 👎
Integrating with the Phishing Initiative API
An official API client is available on GitHub: https://github.com/CIRCL/PyEUPI/
Want more insight into phishing kits?
Start a trial today.
More posts from the Phish Report team
Phishing anti-analysis checks and how to bypass them
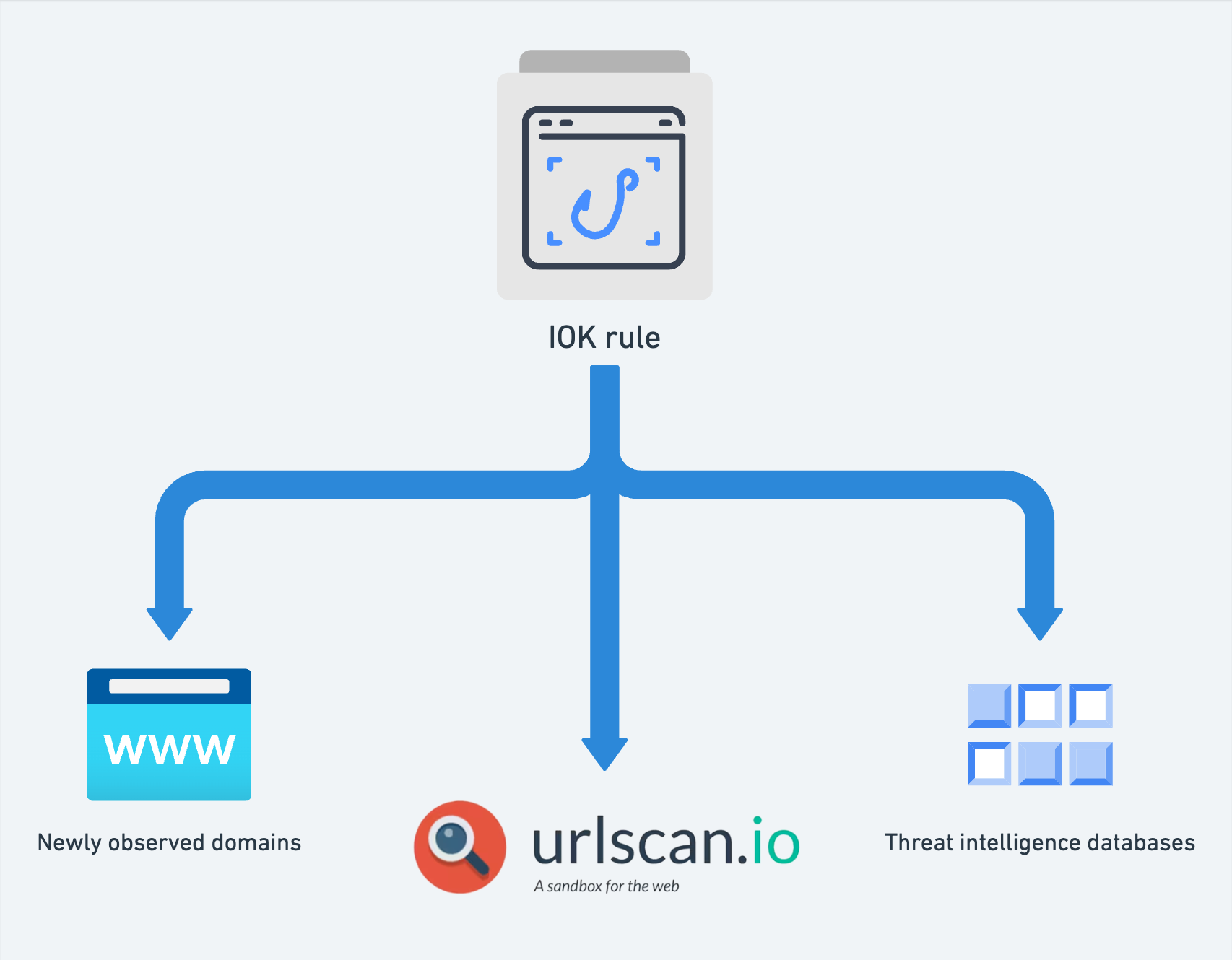
Using IOK rules to hunt for phishing sites across multiple threat intelligence sources
