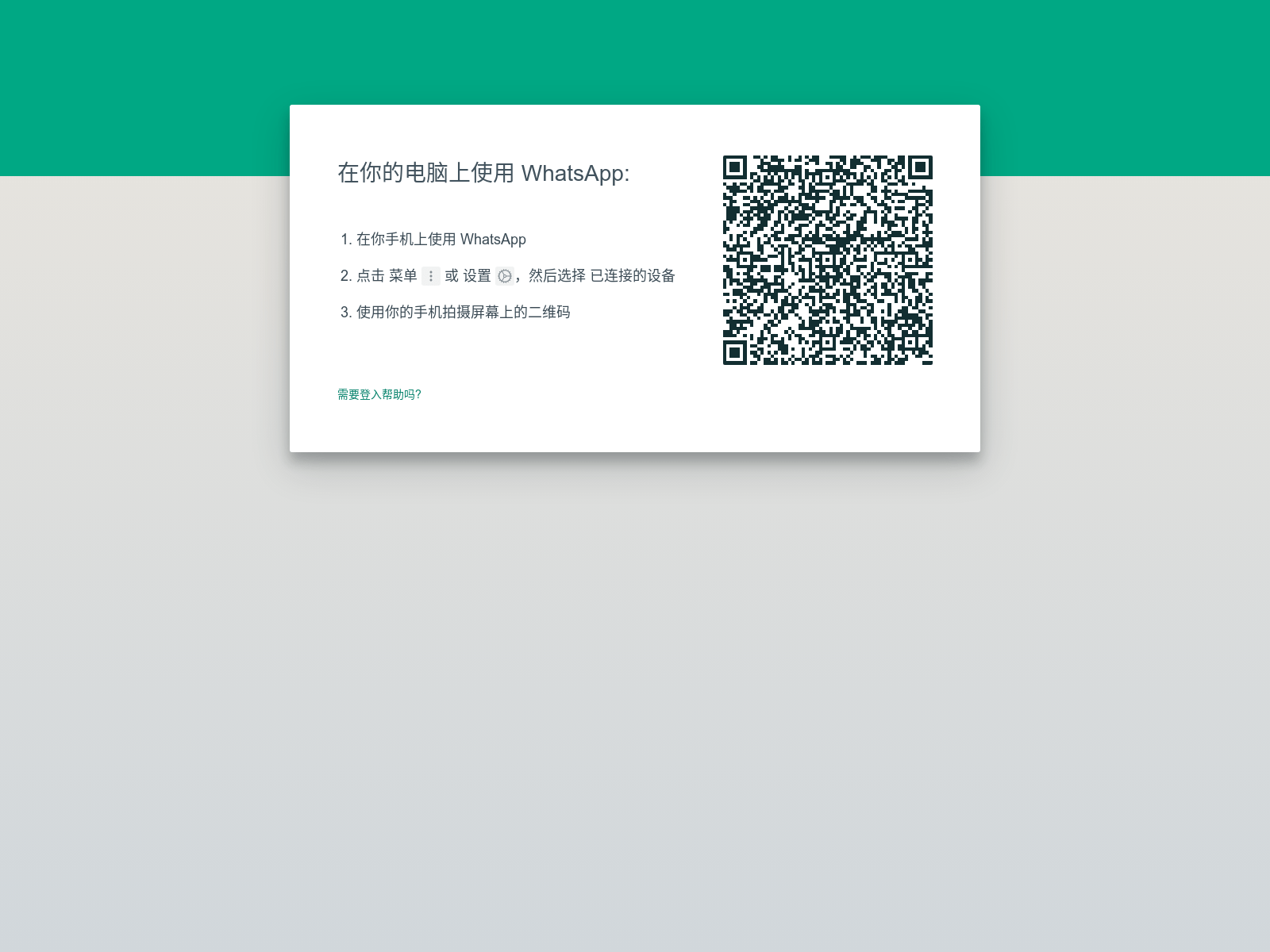
Writing an IOK rule for a WhatsApp phishing kit

Let's write an IOK signature for a WhatsApp phishing kit which targeted Chinese-speaking users for a couple of months in summer 2023.

First off, how was this phishing site created?
(this makes a huge difference to how hard this will be to detect) Lucky for us, this was created by cloning the real web.whatsapp.com page. You can easily tell by the "mark of the web" snippet in the HTML:
<!DOCTYPE html>
<!-- saved from url=(0025)https://web.whatsapp.com/ -->
<html class="js serviceworker adownload cssanimations csstransitions webp exiforientation webp-alpha webp-animation webp-lossless">
...
...
This makes our life much easier because company webpages tend to make many more requests and have lots of idiosyncrasies we can use for detection compared to a phishing page built from scratch.
Our first lead
The first place I always check for phishing kit signature opportunities is the urlscan.io HTTP requests tab. Sure enough, there's a bunch of JS and CSS used by the page which have very unique names.
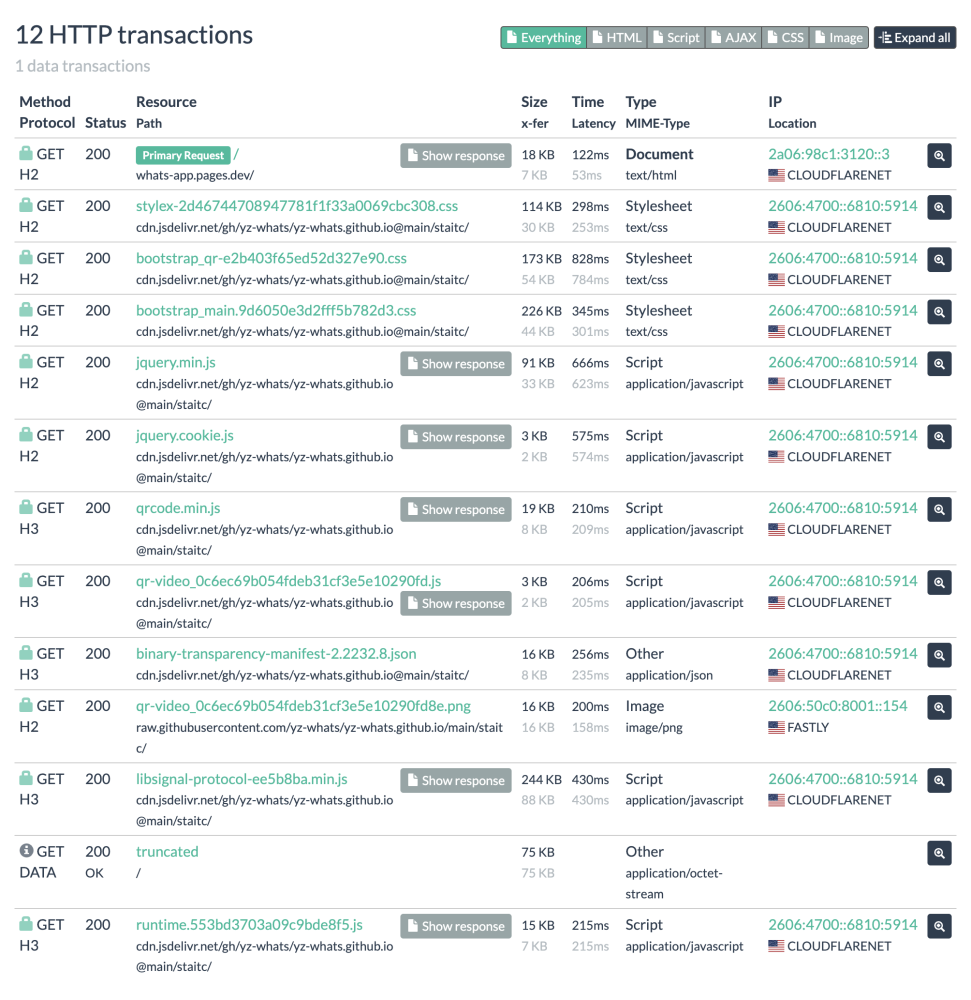
Many of these would work as the basis of an IOK signature, but I'll pick this request:
runtime.553bd3703a09c9bde8f5.js
Looking at other sites that load this filename we can see just 15 results:
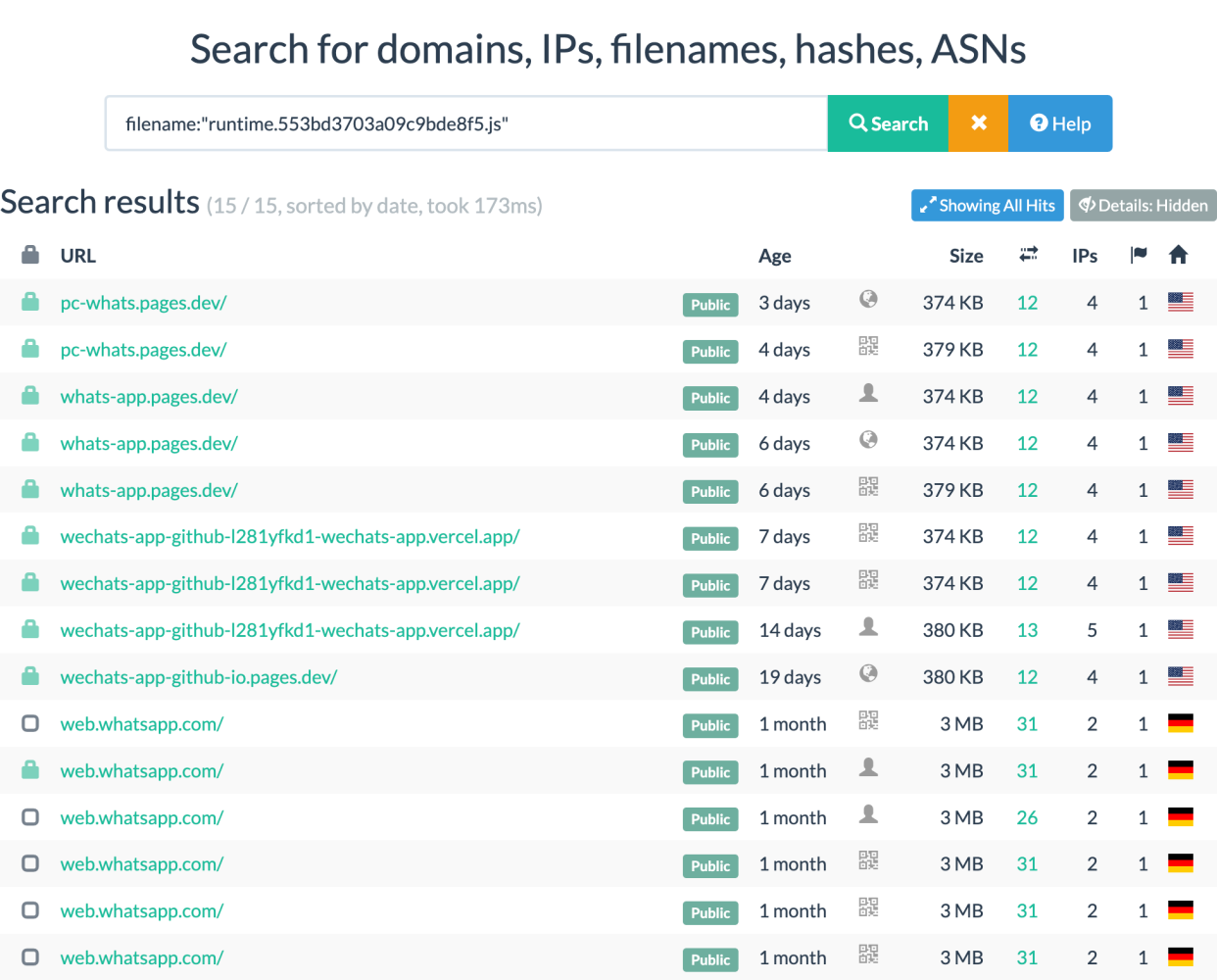
The real WhatsApp Web app was loading a resource with this name, but soon afterwards we see the first of the phishing kits show up.
Writing the IOK signature
To start with our IOK signature for this phishing kit can just match based on that filename:
title: whatsapp-553bd
description: |
A WhatsApp-web themed phishing site targeting Chinese users
references:
- https://urlscan.io/result/3bdee4a6-c6d4-47ca-ad21-fce2a8cccc39/
detection:
resourceRequest:
requests|endswith: runtime.553bd3703a09c9bde8f5.js
condition: resourceRequest
This is already a very high-signal signature, but it's possible there's another WhatsApp phishing site created at a similar time to this one that would also include this filename. How can we detect this specific kit?
Looking deeper into the HTML I see this promising snippet:
<div data-testid="qrcode" class="_2UwZ_" data-ref="2@MaBFYGFMcxIQdLgNUyTeuAujv0Zwx+n7RGCCD+qy3cG5gAiyAa8jdllHrUb95ZWWCq49CFeyTyCbAg==,SeCbFEOy+KEHwLfVEICKZrR9I29yQhQciSyikM4tZko=,xA1RqXwdwn/SmMrI0Xg5snRHRzb8eXnUXpv7aCocsFQ=,C2TqBSNdOTKr2dh3XFq/EI47aNJ4UIlDIR8j6GtOO04=">
This data-ref attribute looks like it might be randomly generated on every page load (and if so, can confirm for us that our signature matches this specific kit and nothing else). Reloading web.whatsapp.com a few times shows that yes, this is a random value! 🎉 So we can expand our detection rule to also check for this value:
title: whatsapp-553bd
description: |
A WhatsApp-web themed phishing site targeting Chinese users
references:
- https://urlscan.io/result/3bdee4a6-c6d4-47ca-ad21-fce2a8cccc39/
detection:
resourceRequest:
requests|endswith: runtime.553bd3703a09c9bde8f5.js
dataRef:
html|contains: '2@MaBFYGFMcxIQdLgNUyTeuAujv0Zwx+n7RGCCD+qy3cG5gAiyAa8jdllHrUb95ZWWCq49CFeyTyCbAg==,SeCbFEOy+KEHwLfVEICKZrR9I29yQhQciSyikM4tZko=,xA1RqXwdwn/SmMrI0Xg5snRHRzb8eXnUXpv7aCocsFQ=,C2TqBSNdOTKr2dh3XFq/EI47aNJ4UIlDIR8j6GtOO04='
condition: resourceRequest and dataRef
Put this into the IOK editor and double check that it works:
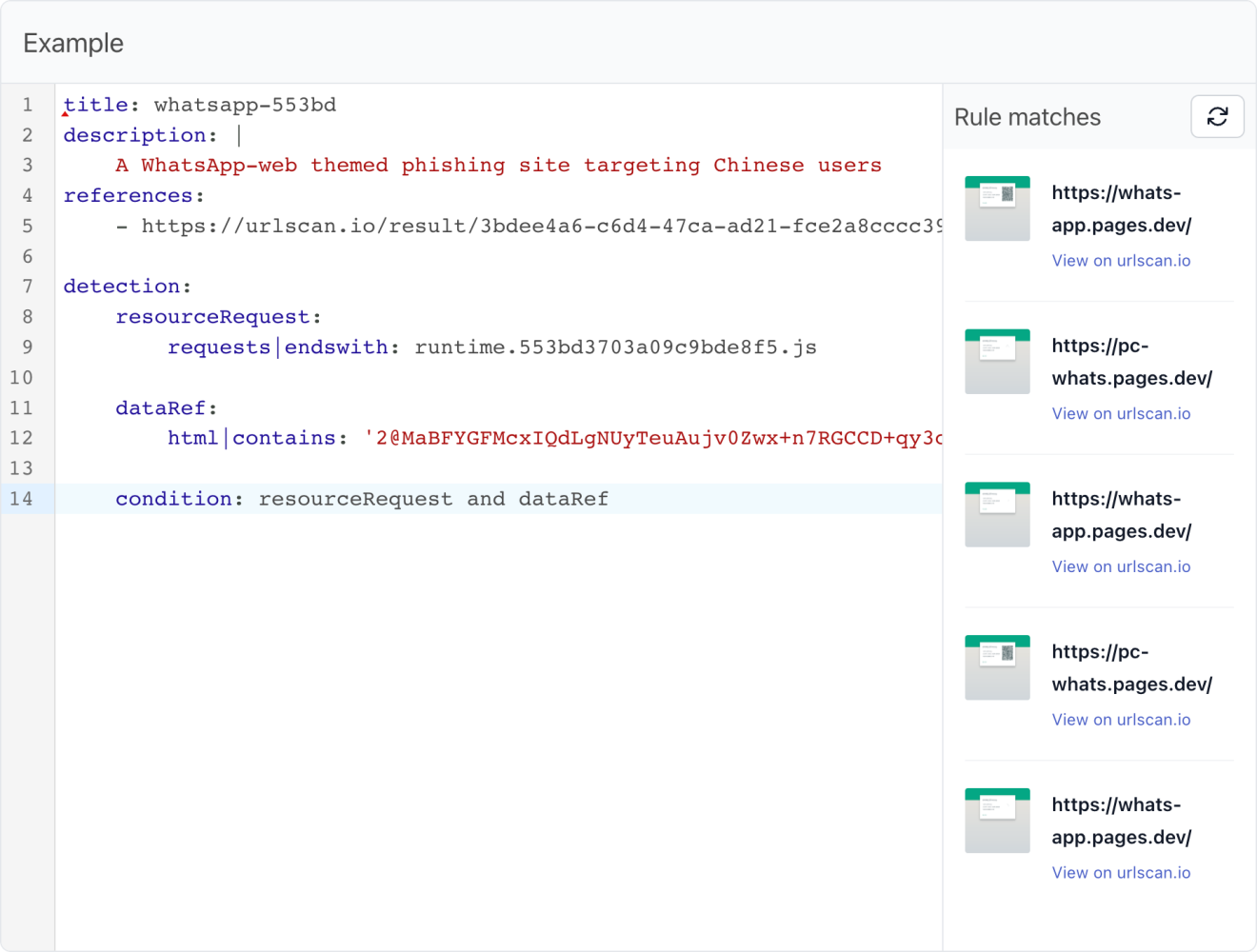
Success 🎉 In just a few minutes and some light poking around in HTML, we've created a extremely high-signal detection rule that will reliably detect this phishing kit for as long as it's used by the attacker.
Want more insight into phishing kits?
Start a trial today.
More posts from the Phish Report team

A startup's guide to phishing and brand protection
How the static site trend has affected phishing