Evading security scanners with fake Cloudflare interstitials

For years phishing sites have been using services like Cloudflare to hide from security scanners, using their anti-scraping features to make automated analysis more difficult.
But multiple phishing kit creators are now using bespoke pages for this purpose, and they're basing their designs on real Cloudflare pages.
Why use a fake Cloudflare page?
Adding an interstitial page like a Cloudflare challenge before your phishing kit loads is a great way to avoid detection. A basic scan of these sites will result in a page like this:
There's no brand logos on this page, no credential collection forms, seemingly nothing that would cause this site to be flagged as malicious. And this really seems to work: sites we found using this technique were often still up and un-detected weeks after creation.
Three examples of fake interstitials
The Phish Report team has identified and is tracking many different variants of these fake interstitial pages, but here's three of the most prevalent:
yochi-cloudflare
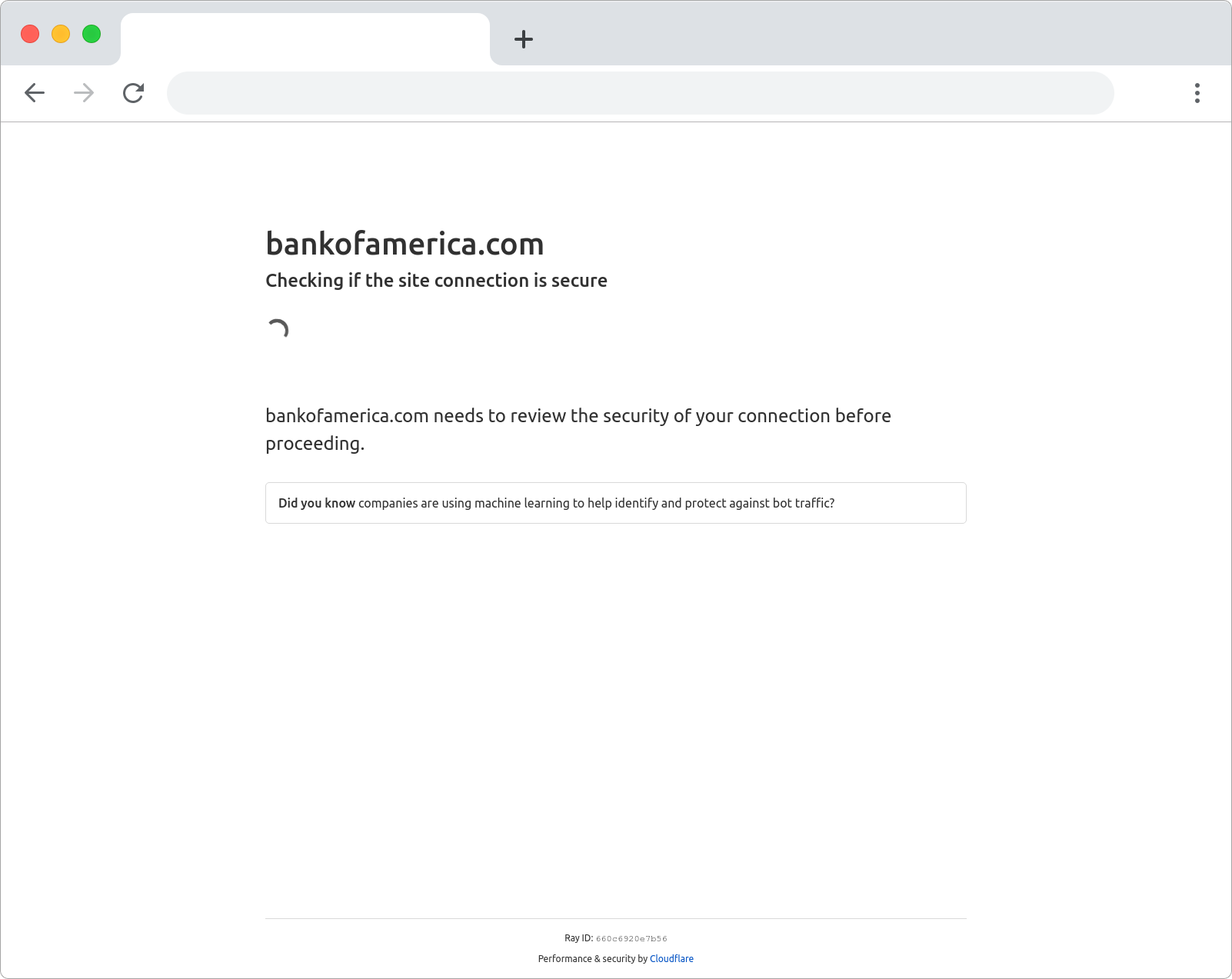
This fake interstitial is used as part of a campaign primarily targeting banks. Most examples we've seen have been sites claiming to be US banks, credit unions, and financial institutions (including Bank of America, Chase, and Fidelity).

yochi-cloudflare pretending to be Bank of America. Although this is hosted on a lookalike domain, the text on the page says that you are visiting bankofamerica.comThese pages set a couple of cookies based on the screen dimensions and redirect the browser to the actual malicious content after a fixed timeout. To evade detection based on DOM hashes, these cookie names are randomised.
<script>
document.cookie = "a568b="+window.screen.width;
document.cookie = "c448c="+window.screen.height;
</script>
<script>setTimeout(function(){window.location.href="874c345/";}, 4000);</script>
These cookies would allow the phishing site to filter out users on desktop browsers, a common anti-analysis technique, but analysis of the backend code shows a simple user-agent based check instead.
if($mobileonly==1 && !in_array($ua['platform'],array('iPhone','iPod','iPad','Android','BlackBerry','Mobile'))){logbot('BROWSER NOT MOBILE');banbot();};
Phishing kit creator
We found over a dozen different phishing kits containing this Cloudflare interstitial functionality, all containing the signature "YoChi".
# <------- YOCHI SCAMA CONFIGURATION FILE <></>
/* ___ ___ _______ __
\ \ / / / _____|| |
\ \ / / / / | |
\ \/ / | | | |___ O
\ /____ | | | ___ \ _
| |/_ _ \ | | | | \ || |
| | o_o | \ \____ | | | || |
|__|\____/ \______| |__| | ||_| grrrr
Telegram : @yo_chi
If you experience any issues or for upgrade
*/
Sightings
- secure4-09authoa[.]com (targeting Bank of America)
- secure297-wellsfargo[.]com (targeting Wells Fargo)
- secure2765-fidelity[.]com (targeting Chase)
An older version of this page (reflecting an older Cloudflare page design) was detected on:
- safegaurd-alerts[.]online
- carburantgouv-info[.]com
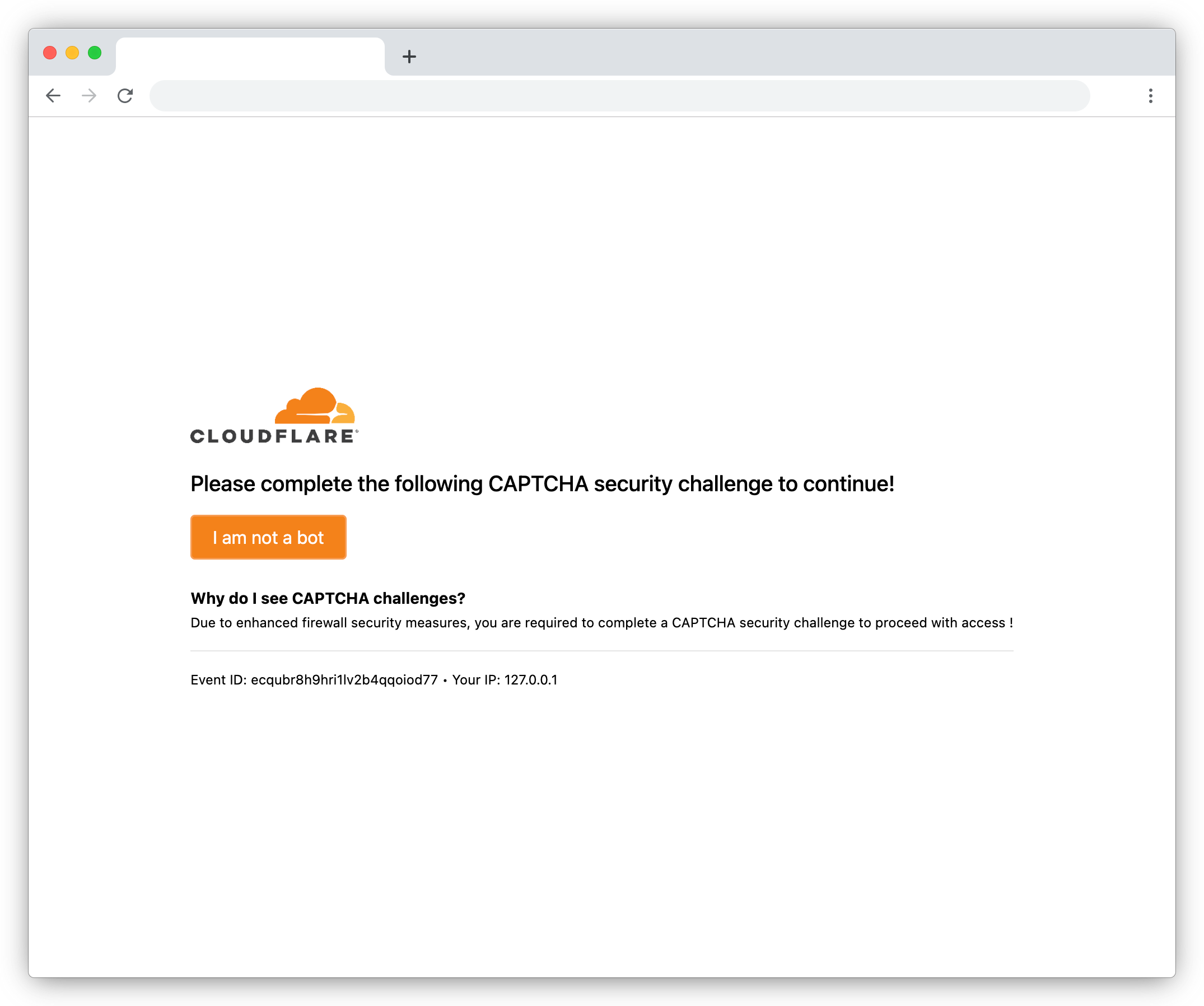
fakeCaptcha
While this page isn't cloned from any specific Cloudflare interstitial, it's very clearly inspired by them, displaying:
- A prominent Cloudflare logo
- An "Event ID" analogous to Cloudflare's "Ray ID"
- The visitor's IP address

Helpfully labelled fakeCaptcha, the "I am not a bot" button reveals this is not in fact a CAPTCHA at all, just a plain button
that takes the victim to the phishing content.
<div class="mb-4" id="fakeCaptcha">
<form method="POST" action="" id="verifyForm">
<button type="submit" class="main-button">I am not a bot</button>
<input type="hidden" name="realPage" value="405c43e5975d8b06fe2f0b20abe280b2">
</form>
</div>
Sightings
This fake interstitial is used across a wide range of cryptocurrency-themed lures:
- nft-palworld[.]jp
- go-worldcoin[.]org
- alpha-magiceden[.]io
- pangolin-tokens[.]com
- tether-drop[.]co
We're yet to obtain the backend code for these phishing kits.
Dark-CAPTCHA
Dark-CAPTCHA is in use by a series of phishing sites targeting cryptocurrency users.
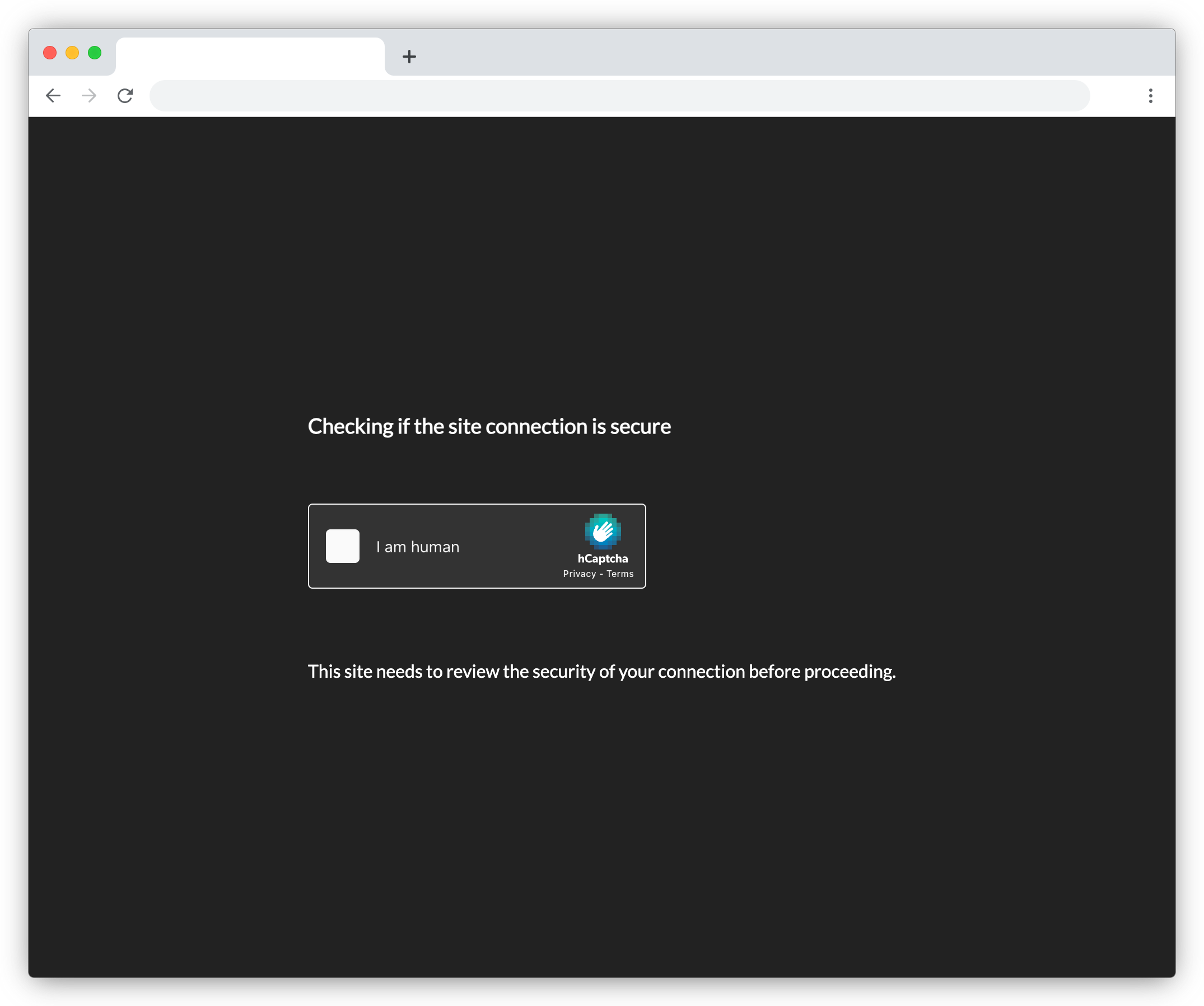
Depending on the phishing kit configuration, either a hCaptcha or reCAPTCHA challenge is presented to the victim.
Rather conspicuously, regardless of the victim's settings, this interstitial is always rendered in dark mode.
Sightings
Dark-CAPTCHA is seen mostly on phishing sites targeting cryptocurrency exchanges, but later versions of the kit added support for phishing iCloud credentials.
- blocked-coinbase[.]com
- safe-icloud[.]com
- 9172647-kraken[.]com
- appie-pay[.]com
- www-help-gemini[.]com
- secure-nexo[.]com
Bypassing fake interstitials
Unlike a real Cloudflare interstitial, these fake versions rarely include actual proof of work or CAPTCHA tests.
Instead, they generally use timeouts (javascript or <meta http-equiv="refresh"> tags) with delays set longer than most security scanners will wait.
You need to be careful to set all the right cookies (yochi-cloudflare will ban your IP if you don't set the right screen width/height cookies), but there's no need to wait the full timeout or solve a CAPTCHA, your scanner can skip straight to the phishing content.
Hunting for fake interstitials
While these pages look like Cloudflare interstitials there's some fairly obvious ways to detect them:
- They don't load the usual proof-of-work scripts used by Cloudflare
- They're not served by a Cloudflare IP!
Here's an IOK rule, matching all the pages shown here, hunting for sites with the title of a Cloudflare page, but which don't load the usual scripts.
title: fake-cloudflare-interstitial
description: |
Sites with the same page title as a Cloudflare interstitial, but which don't load the usual scripts
level: potentially_malicious
detection:
cloudflareTitle:
title: Just a moment...
realCloudflareScripts:
requests|contains:
- /cdn-cgi/
- challenges.cloudflare.com/turnstile/
condition: cloudflareTitle and not realCloudflareScripts
Or the equivalent urlscan.io query:
But, at the rate we're seeing this technique adopted, you'll probably stumble across one soon enough in your investigations...
Want more insight into phishing kits?
Start a trial today.
More posts from the Phish Report team

A startup's guide to phishing and brand protection
How the static site trend has affected phishing