A startup's guide to phishing and brand protection

As a startup, building and protecting your brand is essential to success. Unfortunately, cybercriminals are becoming more sophisticated and are constantly looking for ways to exploit businesses and their customers. One of the most common tactics they use is phishing, which is a fraudulent attempt to obtain sensitive information by impersonating a trustworthy entity. Phishing attacks can damage your brand's reputation, result in financial losses, and harm your customers. In this post, we will provide you with a guide to phishing and brand protection to help you defend your business against phishers:
- Know the types of threat you're going to face
- Things you can do now to harden your brand against future phishing
- What to do when with your first phishing site
- Maturing your response with automation
Is my brand going to be impersonated?
Almost all brands of a certain size get impersonated. But, when your brand gets impersonated depends on how useful it is in helping cybercriminals make money.
If you're a consumer fintech company, expect to see phishing attacks targeting your customers very soon:
- You've got lots of customers for the fraudsters to target.
- Gaining access to your customers' accounts gives the criminals direct access to money so there's no additional steps to monetise their crime.
But, if you're a company offering analytics to businesses you might not see phishing for a long time:
- You have comparatively fewer customers (so it's harder for the fraudsters to target them).
- Even with access to your customers' accounts, it's hard to turn that into money. Instead, you might see sites impersonating your brand that aren't trying to compromise your customers' accounts, but are simply using you as a way to get their credit card details.
Understand how your brand will be impersonated
Phishing attacks come in many forms, and it's essential to understand the different types to defend against them. Some of the most common types of phishing attacks include:
-
Email Phishing: Historically this is the most common form of phishing attack, where the attacker sends an email that appears to be from a legitimate source to obtain sensitive information such as passwords, credit card details, or personal information.
-
SMS Phishing ("Smishing"): This is a form of phishing that targets mobile devices through text messages.
-
Voice Phishing ("Vishing"): This is a type of phishing attack that uses voice or phone calls to trick victims into providing sensitive information.
-
Phishing Websites: In this type of attack, the attacker creates a duplicate copy of a legitimate email or website to trick the recipient into entering sensitive information.
Each of these phishing types needs to be prepared for, and tackled differently.
Hardening your brand against impersonation
Doing some simple steps now can make it much harder for criminals to impersonate your brand in the future.
Make it simple for customers to know it's you
One of the most important steps to get right early on is making it easy for customers to tell apart your brand's real communications from spoofed ones.
Some companies use a dozen different domain names:
- One for their website
- Another one to send emails from
- A third entirely separate domain for a specific marketing campaign
The result is that it's impossible for customers to keep track. Even your security team might need to look twice to spot the difference between a fraudulent domain and one you actually use.
To avoid this, it's important to use a small, consistent set of domain names for your brand. This means using the same domain name for all your communication channels, such as email, social media, and your website. By doing this, customers will become familiar with your domain name and be able to recognize when they receive an email or message from your business.
Likewise, ensure that all your emails, websites, and social media accounts are consistently branded. This includes using the same logo, colors, and fonts across all platforms. Customers are more likely to trust communications that look and feel familiar.
Prevent attackers spoofing your real communications
Set up SPF, DKIM, and DMARC
You probably already have SPF and DKIM set up: nowadays most email servers get you to do this because it helps with email deliverability. While this helps your legitimate emails get through to your customers, it doesn't do anything to prevent spoofed emails. This is where DMARC comes in.
DMARC (Domain-based Message Authentication, Reporting & Conformance) builds on top of SPF and DKIM and tells email receivers how to handle messages which fail these checks.
Postmark have a guide on how to set up and implement DMARC on your domain
If you followed our earlier advice to only use a small, consistent set of domains you'll have a much easier time setting up SPF, DKIM, and DMARC.
Harden your login pages against cloning
Most phishing sites are created by cloning a real login page and then adapting it to create a phishing kit. You can't prevent a website being cloned, but you can add some defenses:
- Install beacon assets: if done properly these evade the cloning process and will call back to your server telling you the URL of any cloned page. You can use canarytokens.org or deploy your own implementation
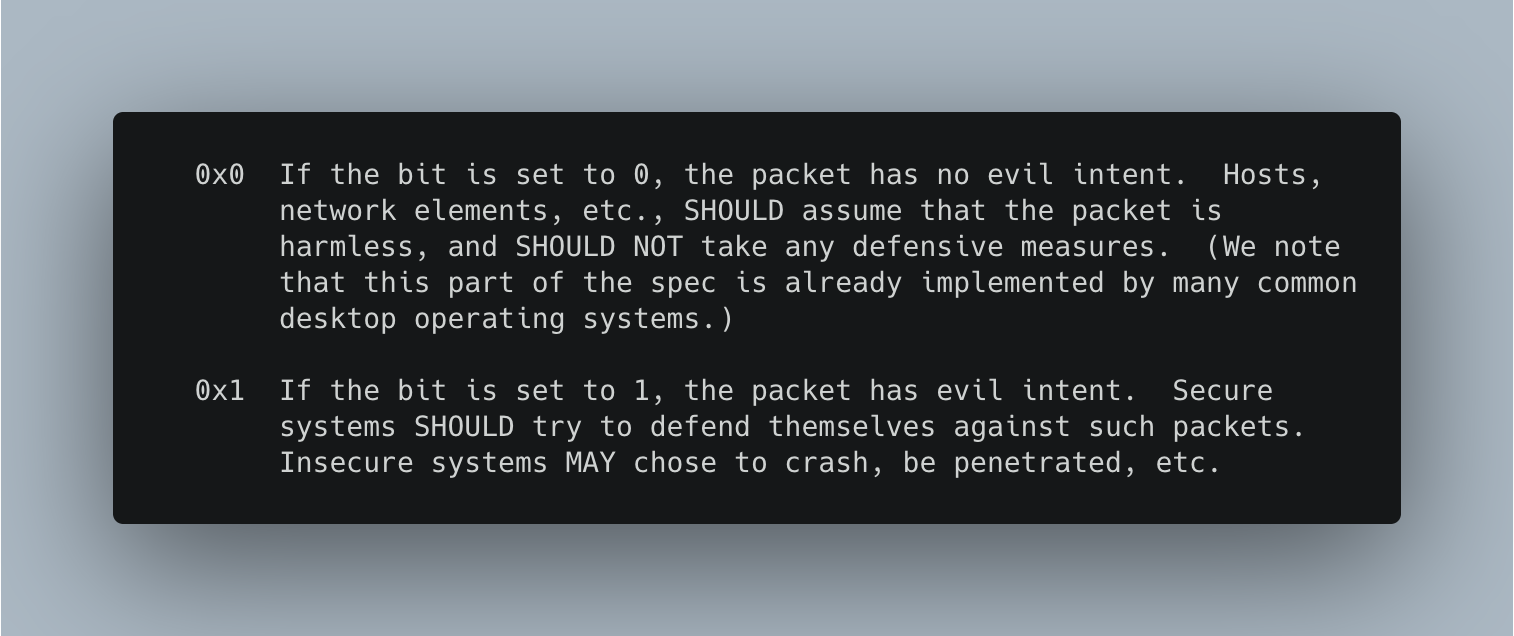
- Embed high-entropy strings: long, random strings are often overlooked by phishers but they make it extremely easy to detect a cloned page
- Don't be generic: if your log-in page is simply titled "Log in" you'll have a hard time distinguishing a clone from all the other login pages out there. Include your brand name to make clones stand out (even if they've changed almost everything else on the page)
Read our full guide on hardening your login page against cloning and spend an hour or so now to save yourself a lot of time in future.
Detecting phishing sites
Once you've hardened your domains against impersonation, you'll need to start detecting phishing sites.
Customer reports
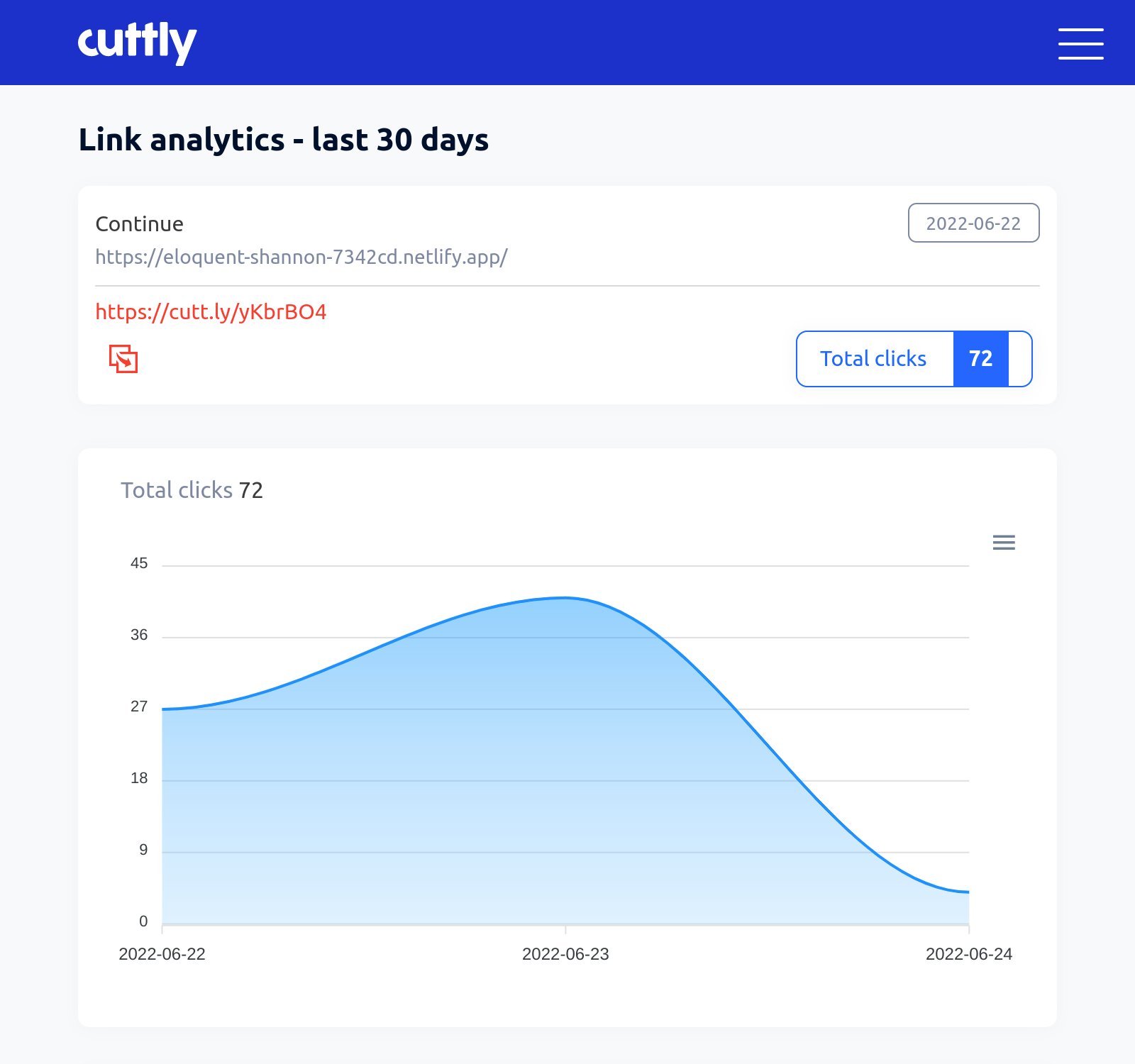
The simplest and easiest way to detect phishing sites is simply listening to reports from your customers. If a criminal is setting up a phishing site impersonating your brand, they're likely sending that site to your customers. Hopefully some of your customers will be suspicious and get in touch with your customer support or security team to check whether it's legitimate.
Finding phishing sites before they reach your customers
Getting reports from your customers about phishing sites is a great fallback, but it's much better to detect phishing sites before they reach your customers.
Thanks to some great data sources, it's actually possible to detect phishing sites within minutes of them being created. We've got a guide on how to start doing this for free today with open source phishing detection tools.
Taking down phishing sites
So you've found a phishing site targeting your customers. How do you get it taken down?
Manually sending abuse reports
There's no secret behind getting phishing sites taken down, you simply:
- Find out who is hosting the site
- Send them an abuse report email or fill out their online form
Find the hosting provider details
There's usually two companies you'll need to contact to take down a phishing site:
- The domain registrar: the company the domain name was registered with
- The hosting provider: the company actually hosting the phishing site
Both of their details can be found using WHOIS data or using our hosting provider lookup tool.
Send abuse reports
Once you know who hosts a phishing site, you simply have to email them or fill out their abuse reporting form. There's usually no automated process here, so a bit of back and forth might be required with their customer support to, for example, provide additional evidence like screenshots of the phishing site.
Want more insight into phishing kits?
Start a trial today.
More posts from the Phish Report team
Detecting phishing sites with high-entropy strings

Top 5 phishing detection APIs you can start using today