The tools your team need to combat brand impersonation
Detect, disrupt, and deter consumer phishing attacks
Phish Report gives you the same capabilities as leading brand protection services and guides you through the takedown process.
- Hosting provider analysis.
- Get verified abuse reporting steps for every provider involved in hosting a phishing site.
- Step-by-step response.
- Guided takedown processes so you always know the best next step in disrupting an attack.
- Rapid detection.
- Get alerted to new phishing sites and begin the takedown process before your users even see them.
Every week, security teams use Phish Report to take down over a thousand phishing sites. Start a takedown
You don't need to be an expert to detect and disrupt phishing attacks, you just need the right tools.
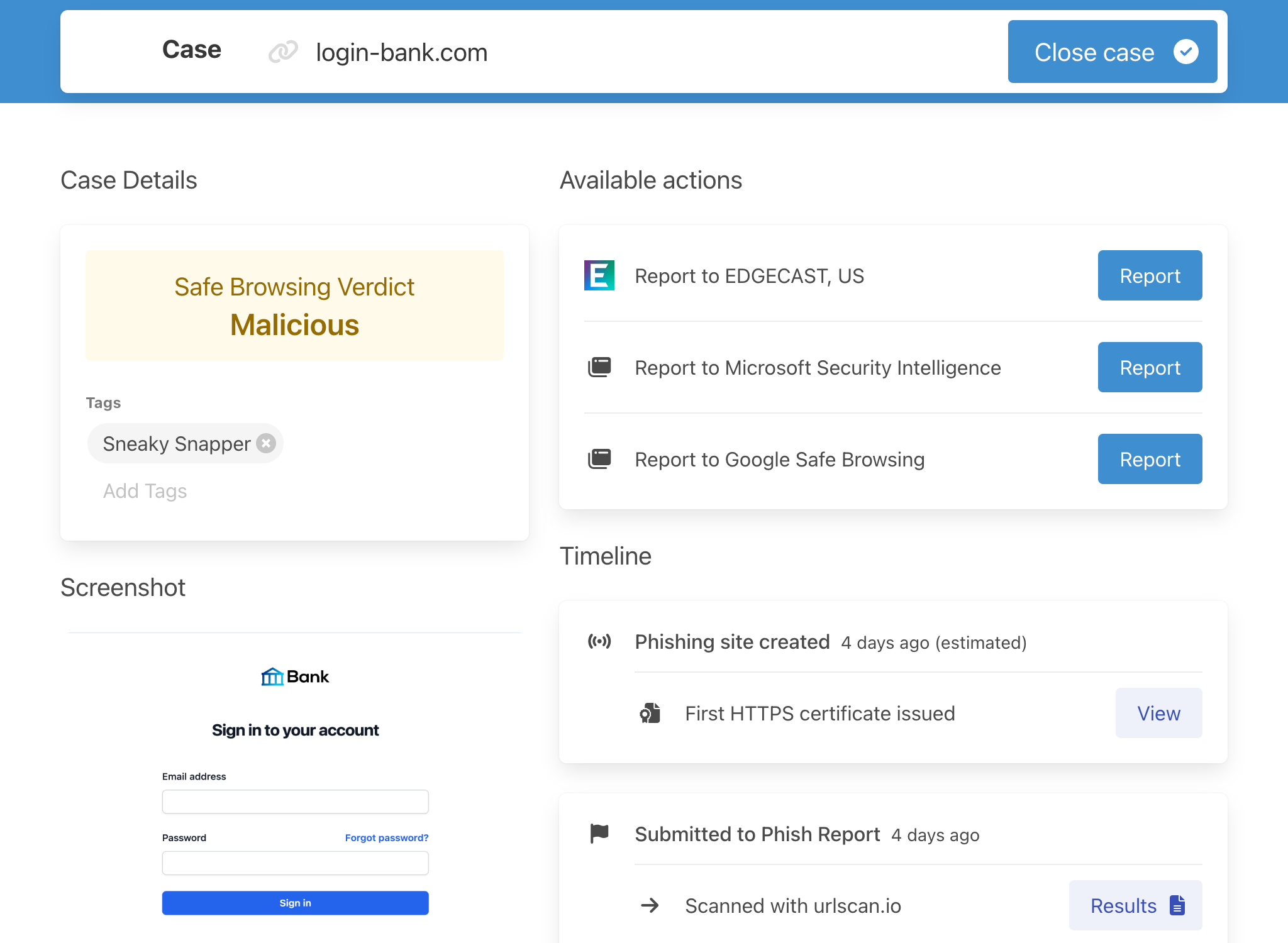
Automated phishing site analysis
Accurate data, without the manual investigation
Are you exploring all avenues to take down a phishing site? Phish Report automatically analyses phishing sites and identifies the best ways you can report it to speed up the takedown process.
- Hosting provider analysis.
- Well beyond naive WHOIS lookups, our verified abuse contact database tells you who's really hosting a phishing site.
- Evidence screenshots.
- Automatically capture evidence screenshots with a real Chrome browser.
- Anti-analysis detection.
- Detect and bypass anti-analysis techniques used by phishing sites to impede your analysis.
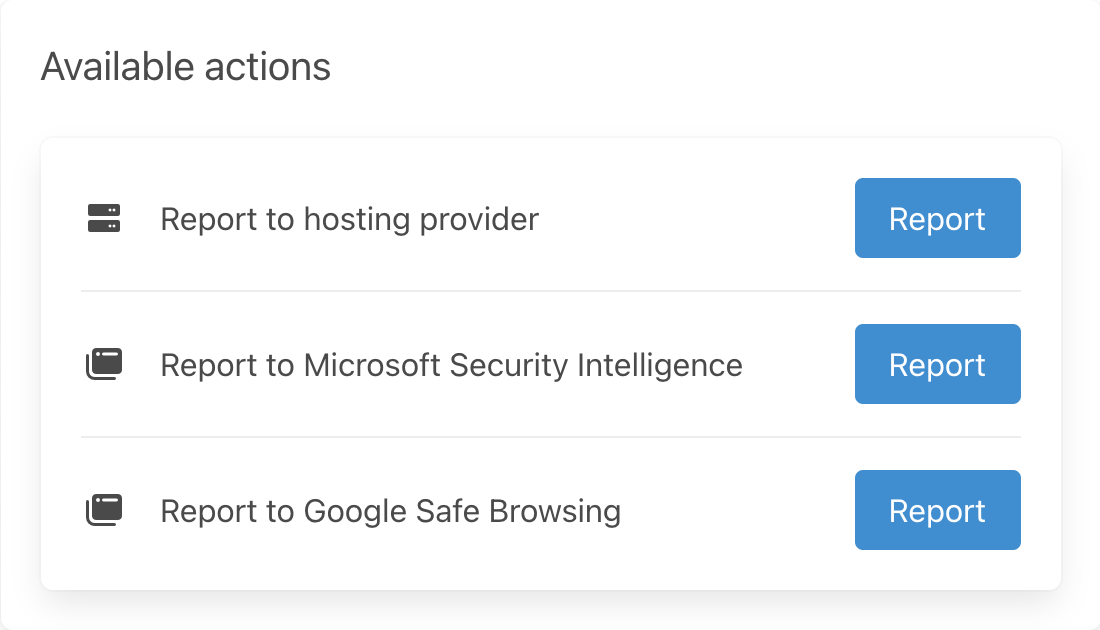
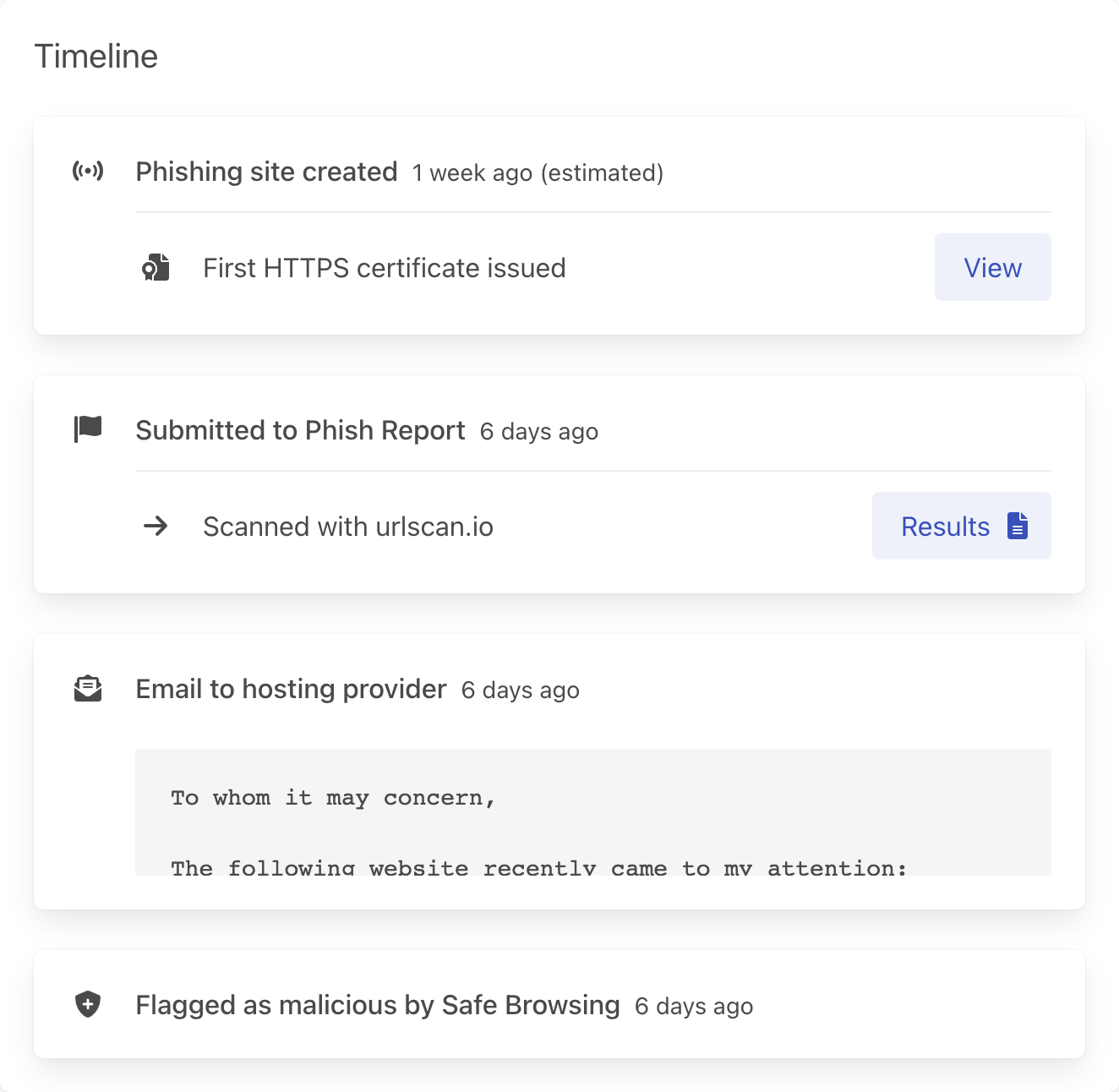
Track the timeline of an attack and be guided through the response
Collaborate on cases with your team
How do you track the status of phishing takedowns? The Phish Report case timeline tracks every report your team sends and the response from the hosting provider. When the site changes or there's additional actions you need to take, we tell you.
- Collaborate on takedowns.
- The case timeline ensures that you aren't duplicating effort and that you're following up with unresponsive hosting providers.
- Understand attack timelines.
- From phishing site creation, to suspension by the hosting provider the case timeline tracks the lifecycle of each phishing site.
- Analyse campaigns.
- Tag cases with threat intelligence and track the prevalence of kits, tactics, and threat actors over time.
Detect phishing sites with our open-source language
Classify known phishing kits and discover new variants
With our open-source signature language, it's easy to create detections for the phishing kits impersonating your brand.
- Millions of domains scanned every day.
- We ingest multiple feeds of new domains and check each against signatures of phishing kits.
- Rapid alerts.
- As soon as a new site matches signatures for your brand, we alert you—usually within minutes of them being created.
- Tuning help from our detection engineers.
- Our phishing experts are available to help you tune your rules and write new ones.
title: Fake Chrome error page
description: |
The Chrome error page HTML is built into the browser: you should never see it in the response from a
website.
This is a clear sign that the site is employing cloaking/anti-analysis techniques.
references:
- https://twitter.com/phish_report/status/1537825544343011328
detection:
chromeHTMLFragments:
html|contains|all:
- '<body id="t" class="neterror" style="font-family: '
- '<div id="main-frame-error" class="interstitial-wrapper" jstcache="0">'
condition: chromeHTMLFragments